A handful of alternative DNS services offer protection from malware, ransomware and phishing. Providers like OpenDNS and Quad9 can blackhole DNS requests for blocking network traffic associated with botnets, phishing and exploits. These DNS providers promise some level of threat protection, but what do they know? Do they know things? Let’s find out!
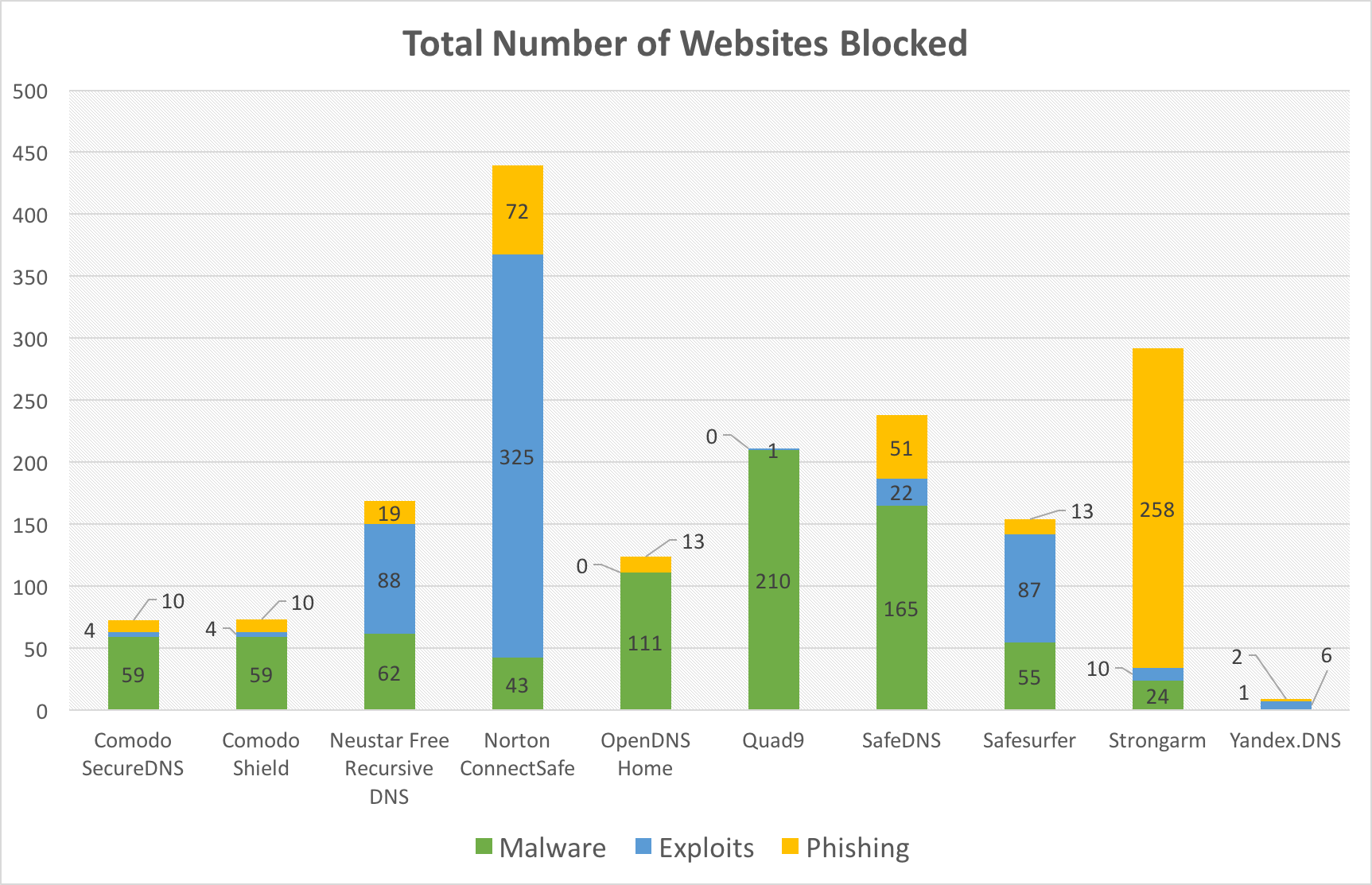
CryptoAUSTRALIA has compared the threat-blocking performance of ten different DNS providers. Our assessment can reveal that Norton ConnectSafe, SafeDNS and Strongarm have managed to block the largest number of harmful websites.
Comparing DNS Providers
In our previous article, we introduced a range of malware blocking and anti-phishing alternative DNS services. Each of those boasts its anti-malware and anti-phishing features, but how do we know which service is the most effective? To our best knowledge, there are no independent tests measuring the actual performance of these services.
Therefore, CryptoAUSTRALIA is releasing a new utility called DiNgoeS today. This tool can measure and compare the actual threat-blocking performance of ten different DNS providers.
How DiNgoeS Works
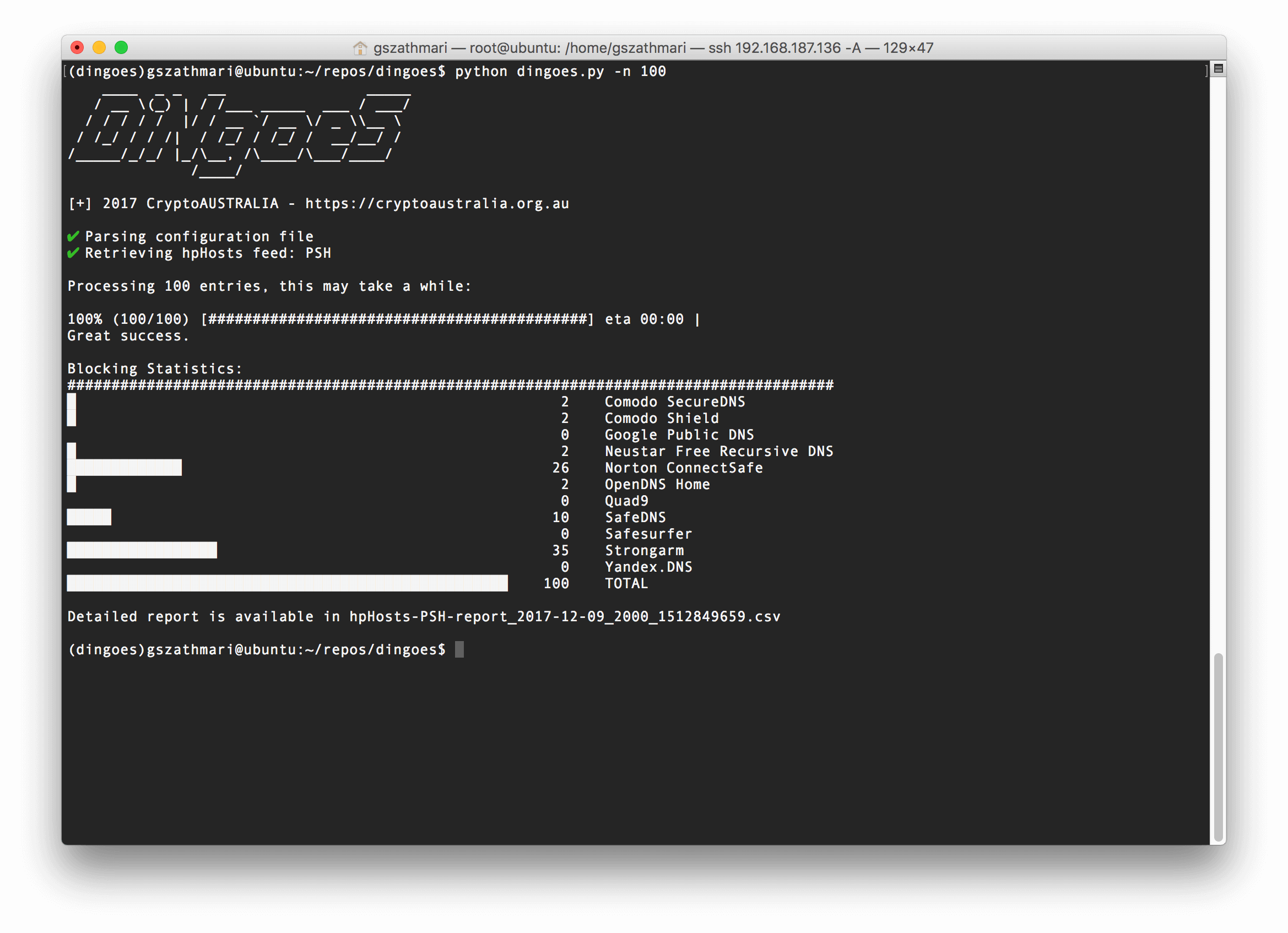
Our new tool is straightforward. DiNgoeS downloads a list of domains known for malicious activity from the hpHosts service first. Then it attempts to resolve each domain with every threat-blocking DNS provider. If DiNgoeS finds that a DNS response is blackholed, it considers the blocking action successful.
Once all domains are resolved, DiNgoeS generates a simple report (as shown below). The numbers show how many domains were successfully blocked by each alternative DNS provider.
In addition to the simple summary, DiNgoeS also generates a detailed CSV report of the threat blocking capabilities. The detailed report can be used for further calculations or trend graphs.
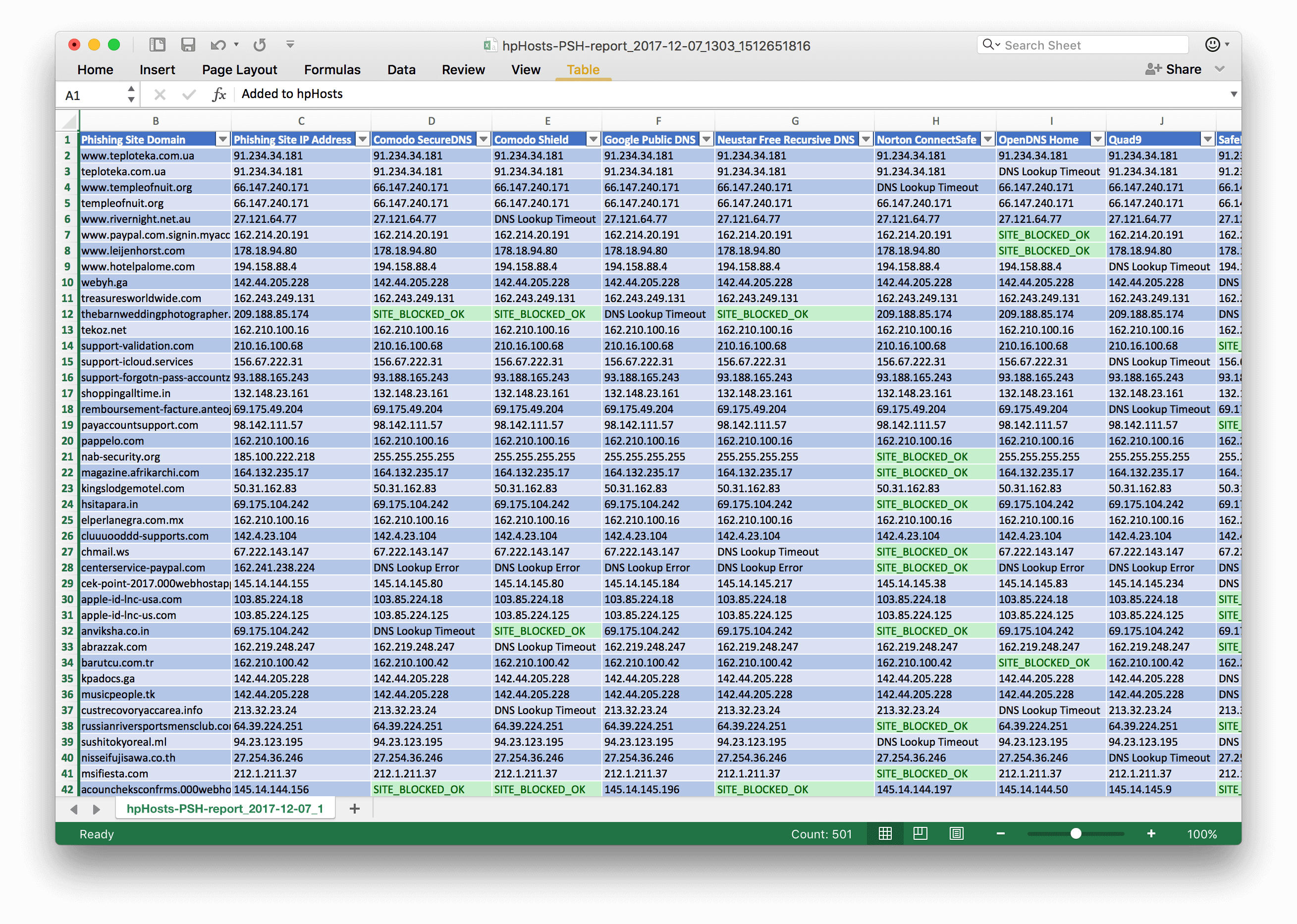
Our tool currently supports OpenDNS, Comodo (2x), Norton ConnectSafe, Quad9, Neustar, SafeDNS, Safesurfer, Strongarm and Yandex.DNS. As for threat data, DiNgoeS relies on three hpHosts feeds: exploits (EXP), malware (EMD) and phishing (PSH).
DiNgoeS is now available on GitHub and pull requests are welcome.
Initial Findings
We pulled a fresh list of 500 domains known from malicious activity (EXP, EMD and PSH respectively) on 23 December, and ran DiNgoeS from four different locations (Sydney x2, Frankfurt and N. Virginia). The reason behind the four scans was to iron out the DNS resolution errors (e.g. network congestion, throttling) by taking the average of the four separate results.
Our first results show that Norton ConnectSafe, SafeDNS and Strongarm has managed to prevent the largest number of threats from the ten providers under this assessment.
The highest number of websites was blocked by Norton ConnectSafe. This service was able to stop the largest number of the threats. Interestingly, ConnectSafe excels at blocking browser and OS exploits. As for its anti-phishing and anti-malware capabilities, the service is as effective as the others behind.
Note that the total number is a bit exaggerated compared to the rest of the herd, as ConnectSafe was hijacking about 300 domains in the EXP category, even though these domains were already offline. We did not correct the results with these false-positives, as other services did exhibit a similar behaviour to a smaller extent
The runner-ups are SafeDNS and Strongarm. Although they both managed to block the same amount of domains, there is a subtle difference between the two services. While SafeDNS did block a significant number of domains associated with malware activity, Strongarm did perform well with blocking phishing content.
The next in the line is Quad9. This service did manage to block a high-number of malware-related domains. The explanation is probably that the block list of this service is based on the IBM X-Force threat intelligence service. Unfortunately, the DNS service did not seem to block too many exploits and phishing domains this time.
The following services are Neustar Free Recursive DNS and Safesurfer. Both services seem to perform all right in the malware and exploits categories. They did not perform well with phishing. To Safesurfer’s defence, it is advertised as an anti-pornography filter, albeit the FAQ claims the service can block malware, phishing and botnet activity as well.
OpenDNS Home performed better-than-average with malware-related domains. Sadly, the exploit-blocking capabilities seem to be inadequate, as OpenDNS managed to block zero domains from the hpHosts EXP feed.
The next two are Comodo SecureDNS and Comodo Shield. They managed to block a fair number of malware-related domains, but they did not block much in the other two categories. Interestingly, the results are quite similar, probably because the same company is operating both of these services.
Finally, the last one on the list is Yandex.DNS. This service has barely managed to block any malicious sites from any of the hpHosts feeds, although Yandex.DNS boasts its malware-blocking capabilities. Maybe the service can block more threats targeting Yandex’s primary audience in Russia.
The Small Print
Our assessment is not meant to be comprehensive, unbiased or complete.
Firstly, we relied on threat data from a single provider only: hpHosts, which was an arbitrary choice. If any of the alternative DNS providers happen to source threat data from hpHosts, it probably distorts our results.
Second of all, occasional DNS resolution errors did occur due to intermittent network issues and throttling. As these errors were unpredictable and random, we ran the scans from four different locations (Sydney x2, Frankfurt and North Virginia) and took the average of the results.
We ran the scan on a single day (2017-12-23), so the results might be different if the scans are rerun at a later date.
Despite these limitations, we believe that the assessment gives our readers a general idea about how the different alternative DNS providers perform compared to each other.
The raw CSV reports generated by DiNgoeS, and our calculations are available to download here. Comments are welcome on Twitter or in private.
Summary
A handful of alternative DNS providers provide threat-blocking capabilities. These services could protect laptops, smartphones and other devices from malware, ransomware and phishing by blackholing DNS requests.
As the actual performance of these threat-blocking DNS providers was previously unknown, CryptoAUSTRALIA has developed a new tool for measuring the effectiveness of these services. DiNgoeS, our new command-line tool, can calculate the total number of domains each DNS service manages to block.
Our assessment found that alternative DNS providers, such as Norton ConnectSafe, SafeDNS and Strongarm live up to the expectations, while other services could improve in certain areas.
This article has first appeared on the CryptoAUSTRALIA blog. CryptoAUSTRALIA is a not-for-profit organisation running hands-on workshops for privacy concerned-citizens and professionals. Sign up for the newsletter or follow CryptoAUSTRALIA on Twitter for the latest updates. Image courtesy of Pixabay.