This article is aimed at helping legal professionals who commonly provide payment instructions for trust accounts and other transactions over email. Providing payment instructions over email puts you at risk of payment redirection fraud. In this article, you will learn why Australian legal professionals are high-value targets for cybercriminals and why you should be concerned. You will learn how and why money transfer scams work, and practical steps you can take to avoid becoming a victim of fraud.
This article is based on the first Cybersecurity for Lawyers by CryptoAUSTRALIA workshop, and was co-written with Jeremiah Cruz and Nicholas Kavadias.
Email Is A Soft Target
Email is an essential communication channel for legal practices, conveyancing practices and most other professional services businesses. On the other hand, email is an inherently insecure channel, and cybercriminals have the financial motivation to take advantage of the design weaknesses of email. Cybercriminals rely on a range of techniques to defraud legal practices by hijacking email accounts and using them to redirect payments either to or from the business.
By the end of this article, you will understand how and why payment redirection fraud works, and what practical actions you can take to avoid you and your practice becoming victims of cybercrime.
Cybercriminals Are Targeting Legal Practices in Large Numbers
According to TrendMicro’s 2017 Cybersecurity report, Australian businesses are the world’s second-biggest target for email fraud. Australian small businesses often:
- do not have dedicated staff to manage technology;
- fail to get the right computer security advice; and
- underinvest in technology and cybersecurity.
According to The National Profile of Solicitors Report (published by the Law Society of New South Wales), 73% of legal practices in 2016 were sole practitioners having similar cybersecurity challenges just like any other small business.
Legal practices, in general, are low-hanging fruit for cybercriminals. Even small suburban practices can deal with financial transactions in the millions. Also, legal practices hold confidential information, such as personal information of clients, including 100 Point ID check records.

What makes legal practices way too attractive to criminals is that:
- financial payment instructions can be easily redirected with an email;
- confidential information can be abused; and
- personal information can be used for identity theft.
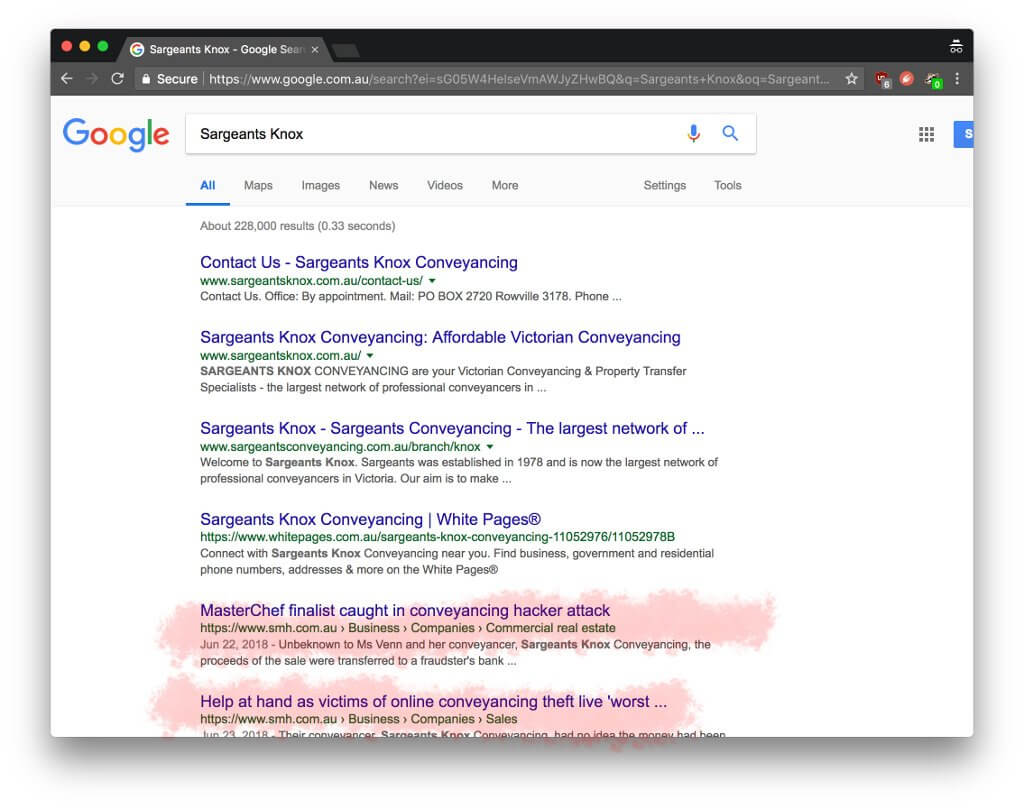
The NSW Law Society has issued multiple warnings alerting legal professionals of payment redirection fraud. In 2017 there were reports of six clients in Western Australia and two in South Australia who were defrauded by payment redirection fraud. There are similar cases last year from Queensland, Victoria and New South Wales. Recently, a there has been the highly publicised case of a former MasterChef finalist and her family having $250,000 stolen from their property settlement on the electronic conveyancing platform PEXA. In all cases, cybercriminals stole money by tampering with the payment instructions.
The Consequences of Being Scammed
Cybercriminals will try to defraud you or your clients. If recent examples are any indication, financial losses to your clients can run into hundreds of thousands of dollars. Being a victim may mean financial losses to your practice, or financial losses for your clients which you are liable for, leading to professional negligence lawsuits, and increased Lawcover premiums.
Did you know that this year, Lawcover purchased cyber insurance for the first time last year, but it only covers up to $50,000?[1] Or that there is pending litigation against solicitors in Queensland, and conveyancers in SA by their clients over losses as a result of payment redirection fraud?
Poor cybersecurity practices that lead to fraud against your clients, or by failing to protect client confidentiality, could lead to regulatory consequences. These may include findings against you for unsatisfactory professional conduct or even professional misconduct.
Finally, the internet never forgets, you and your firm’s reputation can be ruined forever by cybercrime. For example, the name of the conveyancing firm involved in the recent PEXA scandal was widely reported by the media. Today, if you Google the name of the firm, the first page results will show the association of the firm with the fraud. Your firm’s business name associated with fraud on the internet is certainly not good for new business.
Prevention is better than cure. Although damage control is essential when your firm or your clients are scammed, it is best not to put yourself in these situations in the first place. Practices like yours can take steps to protect themselves as well as their clients from payment redirection fraud.
How Payment Redirection Fraud Works
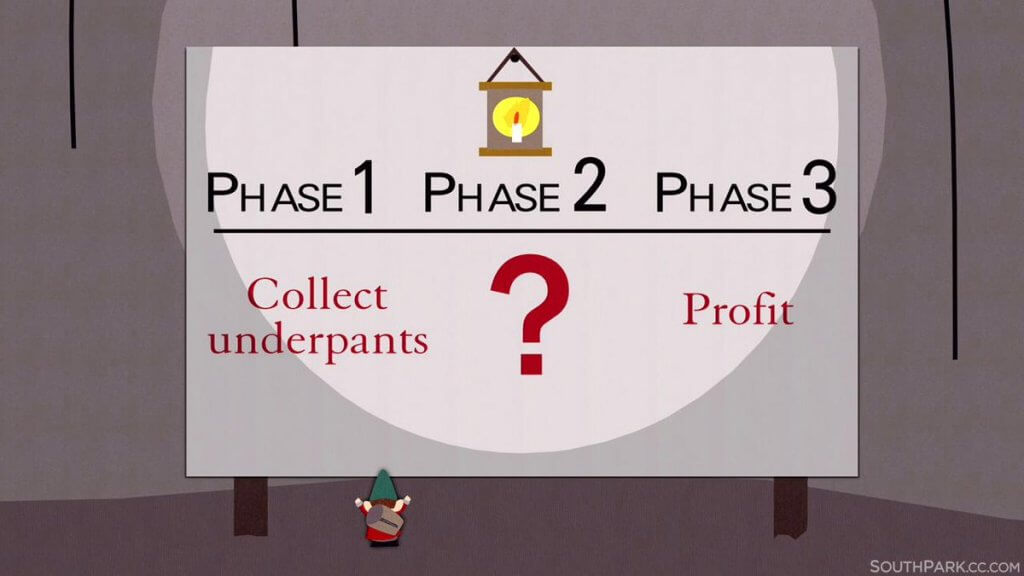
How payment redirection fraud works in three simple steps:
- The cybercriminals get access to your email account ;
- ???
- Profit!! The criminals start tampering with your incoming or outgoing emails to commit payment fraud.
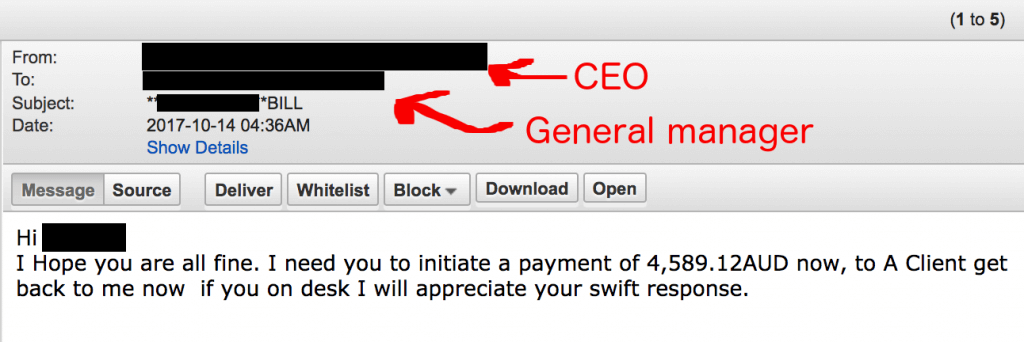
These scams work because criminals exploit the pre-established trust between people. The trust can be abused either between the legal practitioner to the client, or one legal professional to another. Criminals will impersonate one of the parties by email in order to defraud the other.
To impersonate you, the cybercriminals first need to gain access to the mailbox by stealing your login password through a combination of:
- phishing and fake mailbox login pages;
- the mailbox password revealed in public data breaches and password reuse.
Social Engineering and Phishing
Phishing is a cyberattack typically carried out over email. Cybercriminals aim to trick their victims into clicking a link or attachment, giving away their password, or asking them for money by pretending to be a legitimate online service, client, friend or colleague.

Victims of phishing may unwittingly open file attachments containing malware, viruses or ransomware, hand over their passwords to fake websites which look genuine or transfer money to fraudsters believing someone trusted they know has asked them to do so.
Phishing attacks are successful in general because they exploit the way the human minds work. As the “click, whirr” experiment demonstrates, people tend to respond automatically (without thinking twice) when a phishing email asks them to make snap decisions in familiar circumstances e.g. making an urgent payment.
Public Data Breaches and Password Reuse
Industry reports show that one in every two employees is guilty of reusing their passwords across several websites. Sadly, data breaches happen on a regular basis, and passwords are frequently published on the internet for everyone to see.
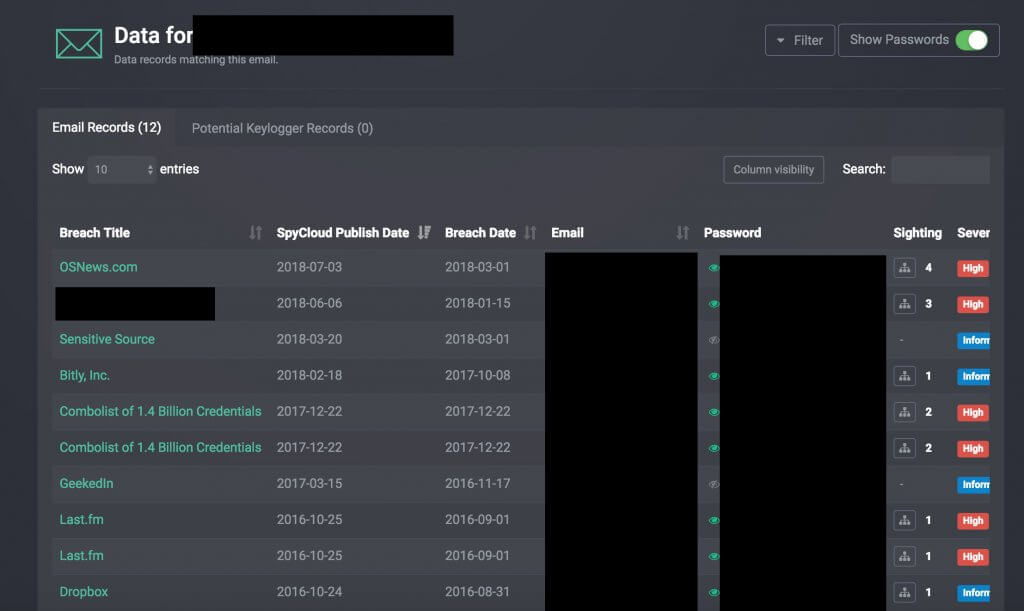
If a cybercrime group targets you or your practice, criminals need to find a valid password first which belongs to one of your employees and use it to successfully log into your employee’s mailbox. This is easier as it sounds. All an attacker needs to do is finding an employee in your business, who:
- was involved in a data breach;
- his or her password was leaked to the public;
- routinely reuses their password across several websites.
The more employees you have, the more likely that one of your employees is reusing their favourite (and leaked) password in your business.
Profit!?!
Once a cybercriminal has access to your business emails, they can move to monetisation. This is done by various methods:
- emailing your clients impersonating you, instructing them that your payment details have changed;
- intercepting incoming or outgoing emails and tampering with the payment details;
- resetting various online account password such as PayPal, LEAP, PEXA; and
- emailing colleagues with malicious links and files with an attempt to compromise additional mailboxes.
Prevention Is Better Than a Cure: How You Can Protect Yourself From Money Transfer Scams
Today’s phishing techniques are no match for outdated pieces of advice , like “be wary of emails with poor grammar” or “never open file attachments from unknown senders”.
First of all, English may not be the first language of your clients. Secondly, your clients send you all sorts of PDF and Word documents – which are a hotbed for criminals to compromise your computer and your mailbox. Changing your passwords regularly will not protect you either. According to recent studies, frequent password changes will only make users choose weak passwords.

What you can do is use the following combination of technical and behavioural changes in your legal practice to protect your firm. We understand that some of the advice may be too technical for legal professionals and if so, we suggest you discuss the advice with your IT staff or your IT service provider or, hire a professional who can understand and implement our advice.
You Can Combat Payment Redirection Fraud With Just a Simple Change: Two-Factor Authentication (2FA)
Probably the most effective (and inconvenient) way to combat payment redirection fraud is a phone confirmation of the financial transactions. NSW Law Societyand Lawcover both encourage everyone to follow this practice, no matter where or how the financial transfer takes place.
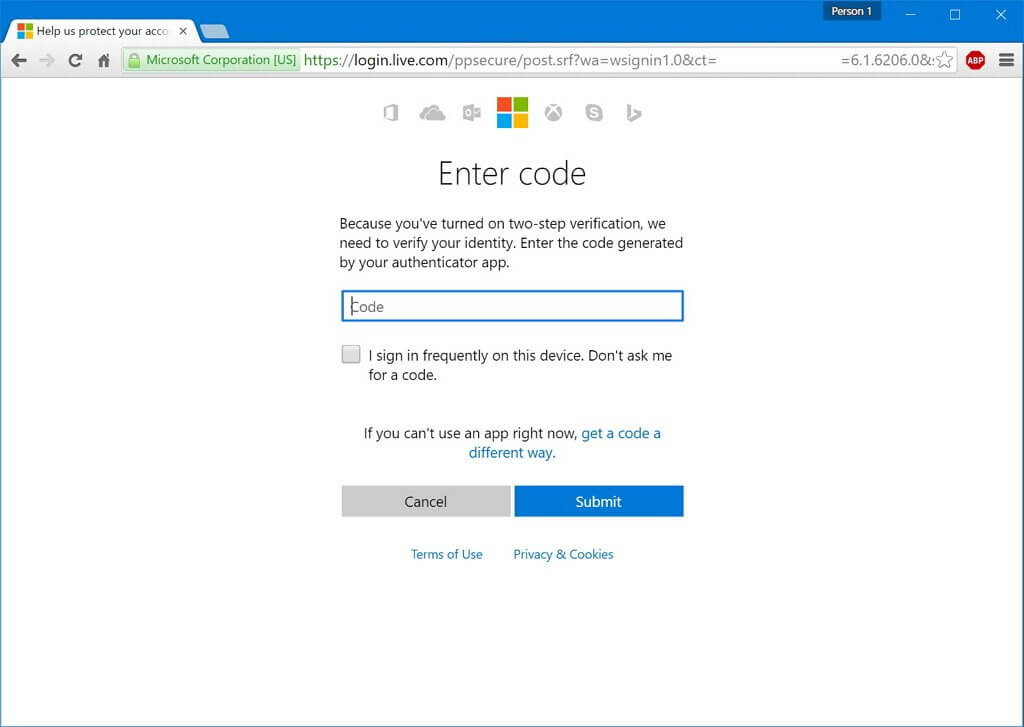
The most effective way we think of preventing your business email from being hijacked is to have two-factor authentication (2FA) safeguard your email accounts. It can protect your mailbox either when phishing steals your password, or if you are guilty of password reuse and your password is leaked in a data breach.
Two-factor authentication, sometimes called multi-factor authentication is an extra layer of security that requires you to key in a one-time PIN, or receive an automated phone call when logging into your email account every once in a while or when you login from a new device, browser, or location. This process may sound tedious, but it is a robust security measure to prevent hackers from hijacking your mailbox.
Services like G Suite and Office 365 already support 2FA features for free. This extra layer of security can be turned on and configured for your email service in under a few minutes.
Convenient devices are also available, such as the YubiKey, which are physical devices you can touch at login and do not require you to enter the six-digit code manually (currently not supported by Office 365).

Technical Changes to Your Domain to Combat Email Impersonation
You can change your firm’s domain name settings to combat cybercriminals sending deceptive emails impersonating your business, which is known as email spoofing. Changing these settings is a little technical, but your IT staff can make these changes. This is done by adding what is known as SPF, DKIM and DMARC DNS records to your company’s domain name.

If you are using Office 365 or G Suite, you are in luck, because Office 365 or G Suite automatically moves any deceptive email to the Junk email folder if the DNS records are set up correctly. You or your IT staff/provider should follow these instructions to create these records for you: SPF (G Suite, Office 365), DKIM (G Suite, Office 365)
The last and most substantial piece of the puzzle is the DMARC record. Contrary to popular belief, SPF alone cannot prevent spoofing. We like the DMARC generator tool of Postmark, this will help you or your IT person craft the perfect record for your domain and also provides you with a weekly email-based report of what may be scammers trying to impersonate your firm’s domain name in their phishing campaigns.
As for emails spoofing the name of the sender only, but not the email address (e.g. My Boss <[email protected]>), have a look on these Office 365 settings or the recently introduced G Suite features. This social engineering technique is also known as ‘Display Name Spoofing’.
Choose a Better (Paid) Antivirus Product
No matter if you have a PC or Mac, you should run an antivirus (AV) product on it. These products can not only detect files with viruses, but the more advanced ones can:
- block ransomware from encrypting your data;
- block your web browser from visiting phishing websites;
- encrypt your network traffic on public Wifi with the bundled VPN service;
- filter spam emails;
- store passwords securely;
- provide advanced memory protection, sandboxing and miscellaneous wizardry that keeps your computer safe from the more sophisticated cyber threats.
You should be aware that not every antivirus product is made equal. Independentreports demonstrate that specific AV products fail to block viruses, which can be devastating if it happens to you. Therefore, we suggest investing in a paid antivirus product that provides you with an above average level of protection, such as:
- avast!
- Avira
- Bitdefender
- ESET
- Kaspersky
When buying an AV product for your business, we suggest you purchase small business editions of these products (e.g. Kaspersky Small Office Security). They usually feature a cloud-based administration panel, where the health of every computer in the office can be monitored from a single location.
Other Ways of Blocking Phishing Attacks
You or your colleagues may receive deceptive web links pointing to password stealing websites via private emails, instant messengers (e.g. WeChat), SMS messages or your website’s Contact us page. It is important to cover these channels as well. Hence we suggest using some combination of the following tools to block access to any phishing websites.
Change your computer’s DNS settings to a DNS firewall service that offers website blocking capabilities. There are free and paid options available. We have covered a range of free threat-blocking DNS services and their relative effectiveness in an article earlier. As for paid products, you may want to consider subscribing to a service like Cisco Umbrella, Cyren or Watchguard. As paid services usually offer a software agent for your computer and smartphones, they can protect your devices even when you are on the road away from the office. If you are geeky, you may want to set up a Pi-Hole on a Raspberry Pi at your office as an alternative.
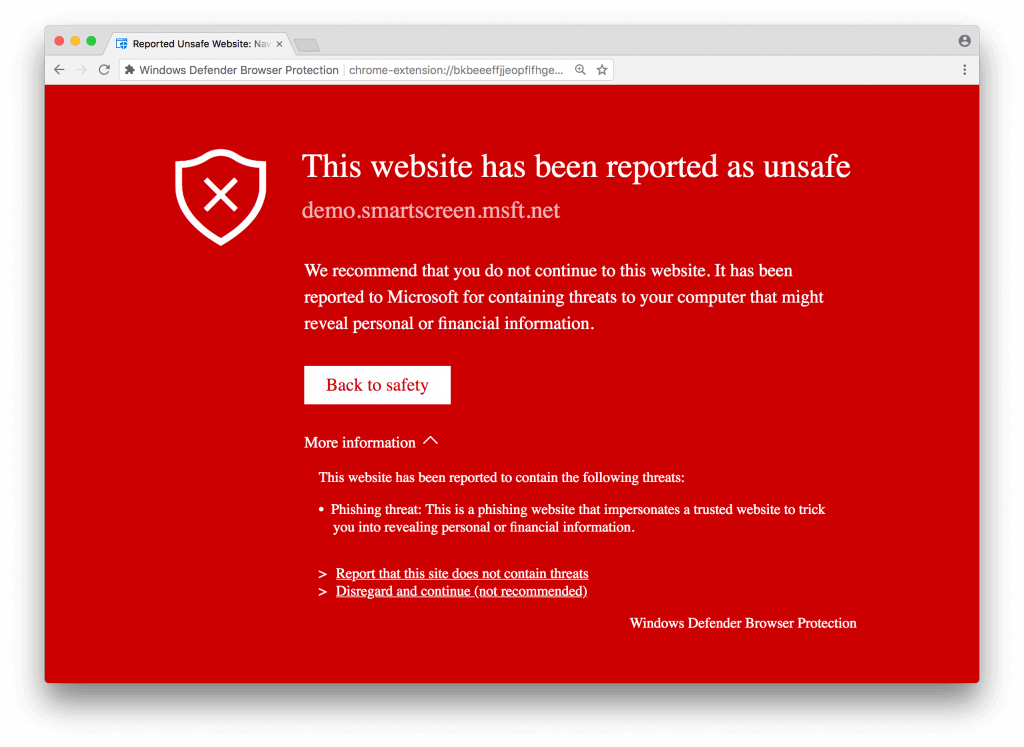
Google Chrome browser extensions like Windows Defender, Netcraft Extension or Blockade can also block malicious websites from being loaded inside of the browser. Other extensions, like Google’s Password Alert extension, can warn you if you enter your G Suite (or Google) password on a fake login page. Firefox also supports the Netcraft Anti-Phishing Extension.
You may also want to consider training your colleagues, as the weakest link is always humans. Industry reports show that 4% of people on average in any given phishing campaign will click on a phishing email. Phishing simulation is a pragmatic approach to identify this segment of your employees, and then you can target them the appropriate phishing awareness training materials. The exercise is very similar to an actual phishing attack. The email templates used in phishing simulations are taken from real phishing attacks.
Anti-phishing services are capable of identifying phishing attempts with greater accuracy than the run-of-the-mill spam filtering which comes free with most email services. Purpose-built algorithms of these anti-phishing services are supported by Machine Learning, Artificial Intelligence (AI) and Threat Intelligence networks, and they look for the specific red flags of phishing attempts, such as typical wording and text semantics, invalid digital signatures, and poor sender reputation. File attachments are also analysed in safe environments for known and unknown threats, and embedded hyperlinks are modified to perform real-time analysis (and block) any malicious URL when the recipient clicks on them.
Anti-phishing services are typically available as separate services, so we suggest you to research what providers are available on the market providing anti-phishing add-ons for your email service.
Conclusion
With 73% of legal firms in Australia being sole practitioners, there is an enormous need for educating the legal profession in cybersecurity best practice. A growing number of cybercriminals target the legal profession way too often with cyber attacks including payment redirection fraud (affecting trust accounts) and ransomware.
We understand that talking to legal professionals about cybersecurity is like talking to millennials about superannuation. This is not an excuse, however, as some of the security measures are either quite easy to implement (e.g. investing into a better antivirus product, not reusing passwords across different websites), or you can hire a professional to do the work for you. You can take some reasonable measures to protect you, your legal practice and your clients from being scammed.
Where To Get More Help
Although it is better safe than sorry, help is available if your firm becomes a victim of cyber fraud. Refer to the Law Council cyber-attack checklist elaborating how to respond and recover from a cyber attack. If you have been hacked, the Lawcover crisis management team can help you clean up the mess. If you have been a victim of identity theft, you should contact IDCARE, which is Australia’s national identity and cyber support service. You should also report the scam to ACCC’s Scamwatch and ACORN. If you need technical help, you should have a conversation with your IT staff or your IT service provider.
Next Events
This article is the first part of a six-part series aiming to educate legal professionals about cybersecurity, and meant to accompany the first Cybersecurity for Lawyers by CryptoAUSTRALIA workshop.
Our second event is now open for RSVPs on Eventbrite.
Make sure to join our Meetup group and sign-up to the CryptoAUSTRALIA newsletterso you do not miss out on the next article and workshop.
Call for Sponsors
We are looking for sponsors! If your legal practice is keen on supporting our initiative, please get in touch with Gabor on our Contact us page and we will get back to you.
About Us
This course was developed by qualified cybersecurity and legal professionals at CryptoAUSTRALIA.
Jeremiah Cruz is a Networking Associate and UTS Graduate. He helps kids learn to code and communicates complex ideas through stories and practical lessons building what he most loves: Games.
Nick Kavadias is a technology and legal expert with over 20 years of industry experience working in industries including telecommunications, banking, retail and healthcare. He has worked in a variety of technical areas including business analytics, information security and software development. He is also admitted as a solicitor in New South Wales.
Gabor Szathmari is a cybersecurity expert with over ten years experience, having worked in both private and public sectors. He has helped numerous big-name clients with data breach investigations and security incident management. In his professional life, Gabor helps businesses, including many small and mid-size legal practices improve their cybersecurity. He is also the president of CryptoAUSTRALIA, the leading authority promoting a society where all Australians can learn to defend their privacy.
This article has first appeared on the CryptoAUSTRALIA Blog.
