A boilerplate for building API services in Restify, CoffeeScript for Node.js.
It is fully documented and Heroku ready. Also features basic security features such as exception handling and input validation.

A boilerplate for building API services in Restify, CoffeeScript for Node.js.
It is fully documented and Heroku ready. Also features basic security features such as exception handling and input validation.
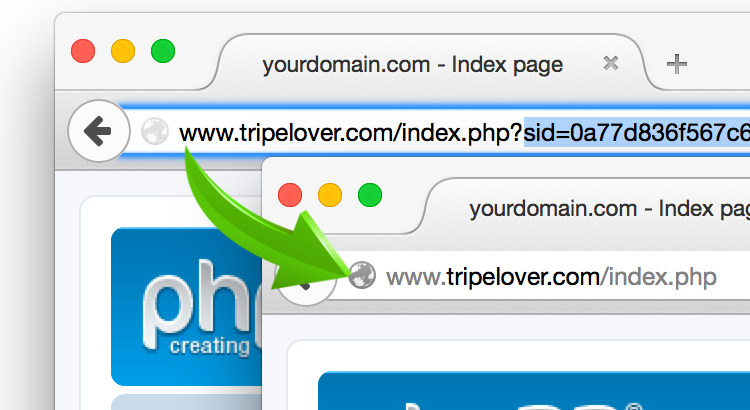
Purge those nasty JSESSIONID and PHPSESSID parameters from the URL bar. Now. Sensitive data in GET parameters are bad. Even over HTTPS.
Check out this session ID killer proxy built on nginx, that converts these sensitive query parameters into safe and secure cookies.

Do you regularly cite The Art of War from Sun Tzu in your cyber security reports? Have you run out of relevant quotes? Today we are proudly announcing our API. It provides an endless feed of bogus, auto-generated quotes from this masterpiece.

Direct access to databases is usually a privilege of DBAs and not end-users. Nonetheless, end-users have to access DBs in certain situations like generating sales reports, making ad-hoc queries, exporting data into spreadsheets and so on. From the security perspective, this is clearly not ideal, as a typical application was never designed to be utilised this way. Instead of saying ‘no’ to […]

In the final part of the series, I am going to show a few practical tips and tricks for protecting your WordPress blog. We have seen earlier how a simple XSS vulnerability can lead to the total compromise of the hosting environment. We not only managed to deploy a backdoor, dump all data from the databases and retrieve each file from […]

We had an XSS vulnerability, we created a fake login page, we stole the WordPress admin’s credentials, now what? Over the following pages, I am going to walk you through the complete data exfiltration process. We are going to get shell access to the OS, dump the databases and configure the compromised WordPress server as a pivot for launching further attacks.