One in three top-tier and mid-tier Australian law firms are susceptible to a cyber threat called “direct email spool attack”, our report can reveal. This lesser-known attack technique bypasses expensive email security solutions, rendering them completely useless and exposing the affected organisations to cybercrime.
This one simple trick means that cybercriminals can completely circumvent email security solutions allowing them to engage in phishing attempts against an organisation unfettered.
This is a multi-part article. Follow this link if you are interested in the OSINT techniques we used to discover misconfigured email gateways and the detailed instructions for setting up a proof of concept email server with the capability to exploit the vulnerability.
Why Australian Law Firms are Exposed to Phishing
Over the last ten years, phishing has become the number one security threat to businesses. Large organisations and businesses in high-risk industries, such as finance, healthcare and legal have responded by purchasing advanced email security solutions such as anti-phishing filters for their email systems. For large organisations, these filters can cost hundreds of thousands of dollars a year.
Earlier this year, we reported that the top-tier and mid-tier Australian law firms had an 83% uptake in advanced email security solutions.
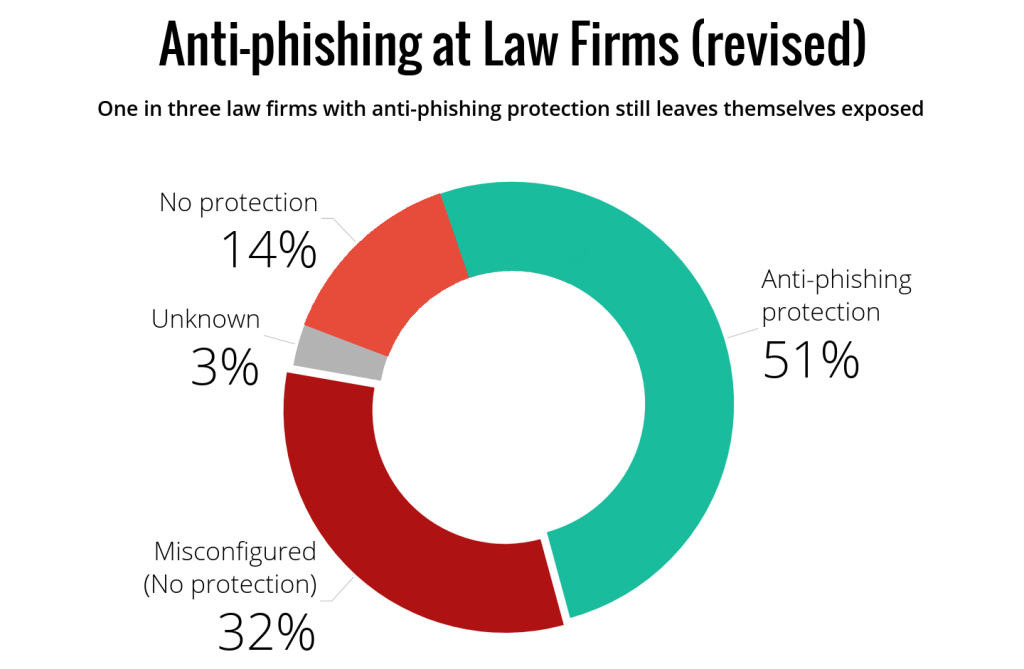
Our research today reveals that out of the 83% of firms which do use email security solutions, more than one-third do not have their email service configured correctly.
This technical blunder exposes these law firms to cybercrime. The situation is made worse by organisations lulling themselves into a false sense of security under the mistaken belief that they have email filtering in place protecting them from phishing and advanced cyber threats.
How Does the Direct Email Spool Attack Work?
To protect an organisation with an email security solution, email administrators need to re-route the incoming emails by pointing the firm’s internet domain name (i.e. DNS MX record) to the upstream email service instead of the local email server (for example Microsoft Exchange) or cloud-based email hosting provider (e.g. Office 365, Microsoft Exchange, G Suite).
All cloud-based email filtering solutions work this way. The DNS change means that incoming emails destined for the firm will be delivered to the email security solution instead of the local email server. Once the emails are analysed for threats, they will then only pass on the safe emails to the email hosting service. As the email analysis all happens outside of the local email service so, the staff do not notice any change in terms of user experience.
The following diagram illustrates the email flow before and after the implementation of a typical email security solution:
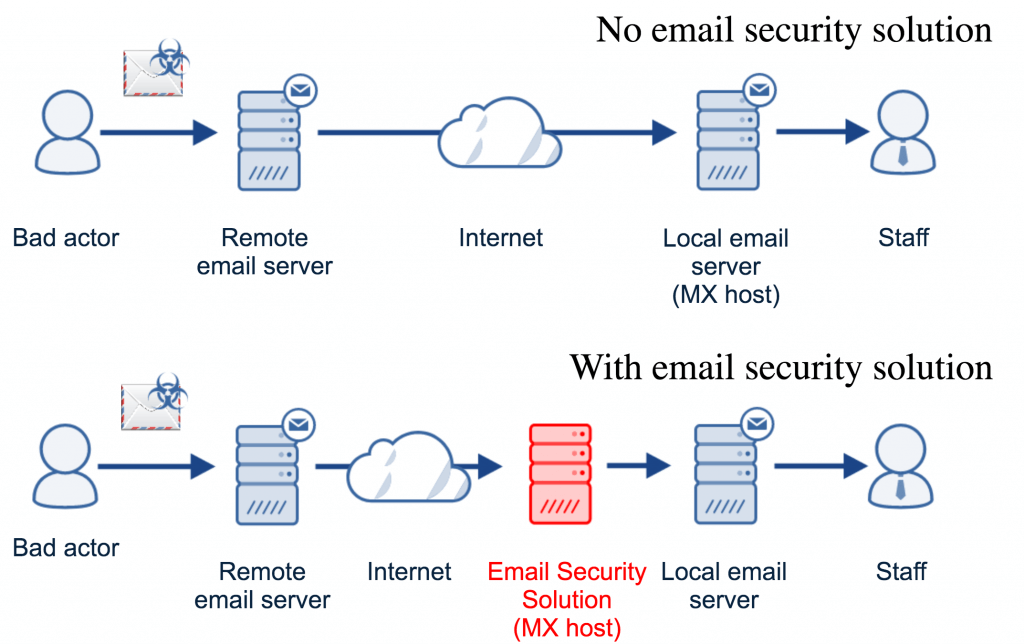
As shown above, every incoming email is normally routed through the local email server (or cloud-based email hosting provider) specified by the recipient’s organisation. As laid down by the email standards, the remote email server looks up the DNS MX records of the recipient’s domain first and then delivers the message to the email server specified by the DNS record.
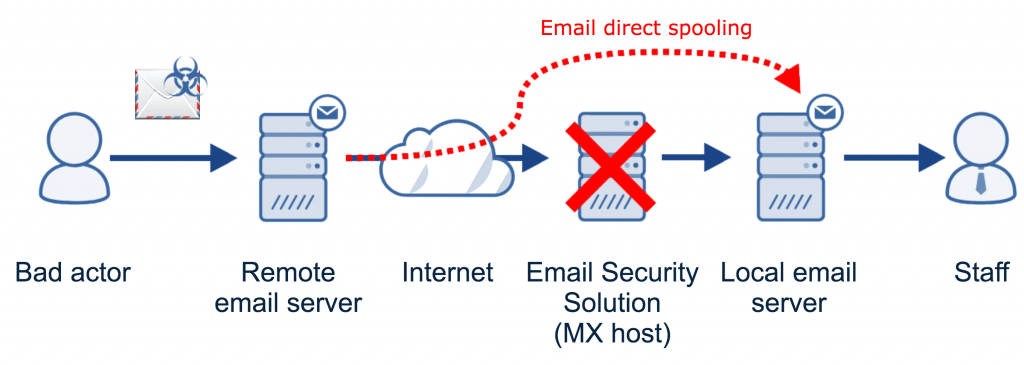
The problem is that criminals do not always follow the rules. Remote senders can skip the DNS MX record lookup phase and feed the emails directly to the local email server instead. This loophole allows bad actors to feed their emails straight into the mailboxes of a vulnerable organisation, bypassing the email security solution midway.
The following diagram illustrates the process of the direct email spool attack:
To prevent this, solution vendors advise that your local email server should be configured only to accept emails from their upstream email security solution. This change is essential to prevent bad actors from circumventing the additional layer of protection.
Vendors including Proofpoint, Mailguard, Barracuda or Mimecast advise customers only to accept emails from the upstream anti-phishing services and publish network ranges to enable administrators to lock down their local email gateways.
However, 31 Australian law firms out of the 79 in-scope of our evaluation failed to implement this vital advice, essentially rendering their email security solutions ineffective against any targeted cyber attack.
How This Vulnerability Affects Law Firms?
The consequences of being vulnerable to the direct email spool attack are twofold. The first is the direct security impact, and the other is financial.
As we reported earlier, many legal and conveyancing practices have implemented email security solutions in response to the explosive growth in payment redirection fraud affecting the industry.
In our experience, we have found that the criminals behind payment redirection fraud are organised crime gangs which are multi-skilled and highly-motivated. Organised crime has the resources at their disposal to adapt to the changing cybersecurity environment and overcome the latest security challenges such as two-factor authentication. Once criminals identify businesses with gaping security holes like legal practices with misconfigured email security solutions, they will exploit these vulnerabilities to make their operation more successful.
Paradoxically, the false sense of security makes staff more susceptible to phishing attempts which bypass filtering. Employees and management may be overconfident in thinking that every single email delivered to their mailbox is free from cyber threats as they all have been thoroughly vetted and scrutinised for malicious intent by the email security solution. If bad actors were to feed emails to the mailboxes, staff would carelessly open and click on emails that did not go through the vetting process as usual.
Lastly, large sums of money are wasted. With more than 10,000 solicitors in Australia working for big law firms and the average subscription cost of any email security solution being about $5 per month, it is safe to assume that these firms are wasting tens-of-thousands of dollars on a monthly basis on subscription costs alone. The money down the drain is considerably more if we consider the Total Cost of Ownership (TCO) such as acquisition costs, operating costs and personnel costs.
In summary, one-third of the top-tier and mid-tier legal practices are failing to protect their staff (and indirectly their clients), because they:
- Fail to implement email security solutions securely;
- Give staff a false sense of security due to the lousy implementation of said technology; and
- Waste hundreds of thousands of dollars per year on a piece of technology that can be bypassed with one weird trick!
The Origins of the Direct Email Spool Attack
The various email standards were developed in the 1980s when security was not a concern. Back then, the internet was a quaint and friendly place. Email servers were open to everyone to send emails (called open relays). This practice was later abandoned due to the abuse by spammers. This relay feature is essentially why our attack can work as it exploits a design weakness of the SMTP protocol.

This attack is known in spammer circles as a way to get around anti-spam filters. For example, if a company website is hosted on www.example.com, spammers may try to get around the anti-spam service by feeding emails directly to the email server at mail.example.com.
Security professionals are also known to rely on this technique in penetration testing engagements to assess email gateways security or to improve the success rate of social engineering attempts. However, this methodology is not common knowledge as far as we know as the practice seemingly lacks any extensive documentation and is not supported by a myriad of purpose-built penetration testing tools.
The attack is so arcane that in our research we did not manage to discover a widely accepted naming convention for it. For example, while MXGuarddog names the attack technique as ‘Direct Delivery’, KnowBe4 calls it ‘Smart Hosting’. To make it easier to refer to this attack, we have named this circumvention technique as “Direct email spool attack” in a modest attempt to coin the terminology. This is a humble attempt to reference the practice of backup MX services spooling emails back to primary email services after outages.
In parallel to this report, we are also publishing the various OSINT techniques we used in this research along with in-depth technical instructions for setting up a proof-of-concept email delivery infrastructure for the benefit of the information security community.
What is Phishing?
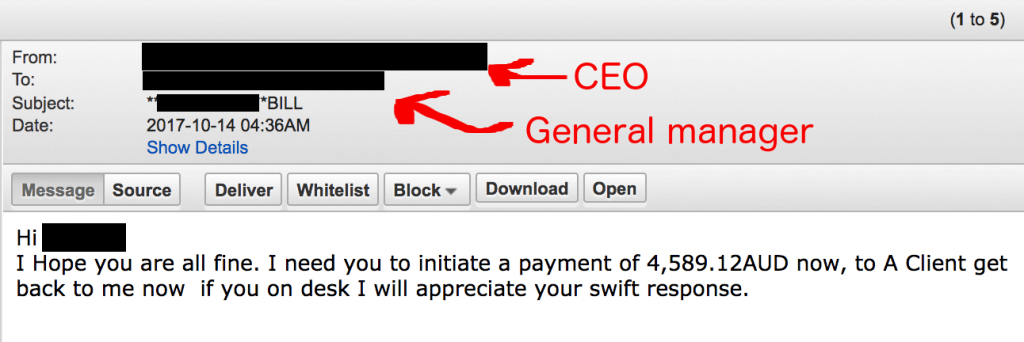
Phishing is a cyber-attack typically carried out over email. Cybercriminals aim to trick their victims into clicking a link or attachment, giving away their password, or asking for money by pretending to be a legitimate online service, client, supplier, friend or colleague. Victims may unwittingly open file attachments containing malware, viruses or ransomware, hand over their passwords to fake websites which look genuine or transfer money to fraudsters believing their boss has asked them to do so.
The potential consequences of a cyber attack arriving in emails are:
- you and your clients are defrauded;
- have your passwords and payment details stolen;
- have your data held to a ransom;
- have your client’s confidential information stolen and sold on the dark web;
- have hackers impersonate you and contact your clients; and
- have all of your emails and documents maliciously deleted or permanently encrypted.
How Email Security Solutions Protect Businesses?
Email security solutions, also known as “advanced threat protection”, “anti-phishing filter” or “advanced email security”, are specifically designed to protect organisations from sophisticated phishing threats. They usually feature advanced technologies such as Machine Learning (ML) and Artificial Intelligence (AI) and algorithms developed to identify phishing attempts.
Email security solutions look for the specific red flags, such as typical wording and text semantics, invalid digital signatures, and poor sender reputation to identify suspicious emails. File attachments are also analysed in safe environments for known and unknown threats, and embedded hyperlinks are modified to perform real-time analysis (and block) any malicious URL when the recipient clicks on them.
In a nutshell, solutions are meant to pre-screen incoming emails for malicious intent before they are passed on to the underlying email hosting platform. Deploying email security solutions to protect you from the latest cyber threats can be implemented alongside a business’s existing email service whether it is cloud hosted on Office 365, G Suite or self-hosted.
Conclusion
Our report from earlier this year found that most of Australia’s top-tier and mid-tier law firms were well prepared in defending against phishing attacks. We concluded back then that the more prominent firms recognise the sheer scale of phishing threats, and have taken action to protect themselves. Our report today, however, sheds new light on these figures. With the addition of the firms susceptible to direct email spool attacks, half of Australia’s leading law firms have no effective email security solution in place to protect them from sophisticated phishing attacks.
Email security is a complicated matter, and there is no silver bullet to protect an organisation from the phishing threat. Phishing is a technology and human problem that must be addressed by a combination of anti-phishing technology, brand monitoring services, threat-intelligence services, staff phishing simulations and phishing awareness training.
Complexity is the enemy of security. Even if an organisation gets the pieces of the email security puzzle right, the actual implementation often fails them – as this report demonstrates. There are too many moving parts and general information technology staff either lack of the technical expertise or the necessary experience in the area to get email security right.
Due to the high number of cyber criminals targeting Australian businesses with payment redirection fraud and Business Email Compromise (BEC) fraud, we urge you to audit your email gateways and the associated security solutions at your organisation as soon as possible.
Is your company affected by direct email spool attacks? Contact us today and we will help you find out.
This research was a collaboration between Gabor Szathmari and Nicholas Kavadias.
