How can you protect your family from malware and phishing with just a little effort? Various alternative DNS services with built-in threat blocking capabilities are now available to the public. This article introduces these public DNS services and helps you pick the right one for keeping your devices safe and secure.
There are different products and services available for blocking malware, ransomware and deceptive websites, including a myriad of anti-virus software, the Google Safe Browsing browser integration, or browser plugins like Blockade. In our previous article, we introduced a handful of block lists that gives an additional layer of protection for your Pi-hole.
Sophisticated Threats
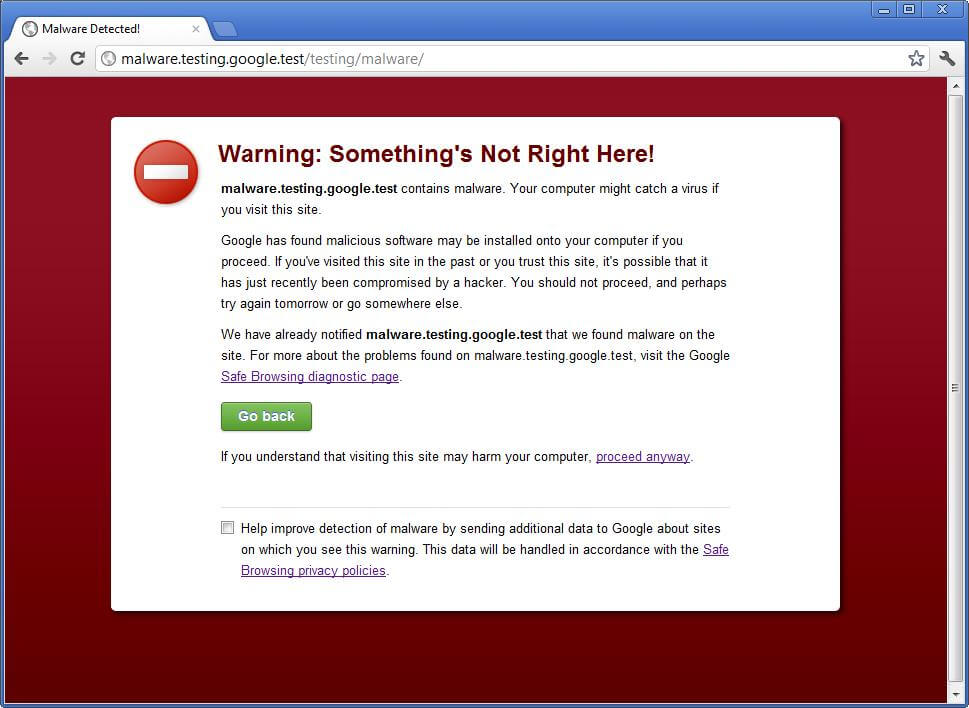
Anyone can inadvertently navigate to deceptive websites, and the purpose of these products is to prevent the web browser from loading the webpage or downloading a file.
How do these mistakes happen? Deceptive emails may contain web links pointing to pixel-perfect copies of login pages, or malvertising can load fake Flash updates or exploit kits in a hidden iframe. These attacks are getting more and more sophisticated, so out-of-date pieces of advice such as “do not click on links in emails with poor English” are becoming less relevant.
Block List Issues
Furthermore, each website blocking technique (anti-malware, Google Safe Browsing, etc.) has its limitations, so it is a sensible decision to rely on multiple layers of protection.
The first issue is the delay. The latest WebRoot Threat Report suggests that “84% of all phishing sites last less than 24 hours”. In other words, time is crucial: the sooner a website gets on the block list, the better. As standard blocking services (Safe Browsing, anti-malware products, etc.) acquire reputation data from different sources, malicious domains may end up too late on their block lists.
Secondly, none of the website blocking services is meant to be comprehensive. While more cautious providers may prefer to keep their customers happy by keeping false-positives low, others may focus on blocking targeted attacks only. The block lists are curated by humans one way or the other, which inherently makes the block lists biased.
Because reaction time is crucial, and block lists are not comprehensive, we should not rely on a single technology.
DNS Based Blocking
As we learned on the Pi-hole workshop, DNS blackholing is a technique that can be used for blocking malicious activity. The Pi-hole blocks ads, trackers, C2 and phishing domains by responding to DNS queries on the block list with NXDOMAIN (i.e. domain not found).
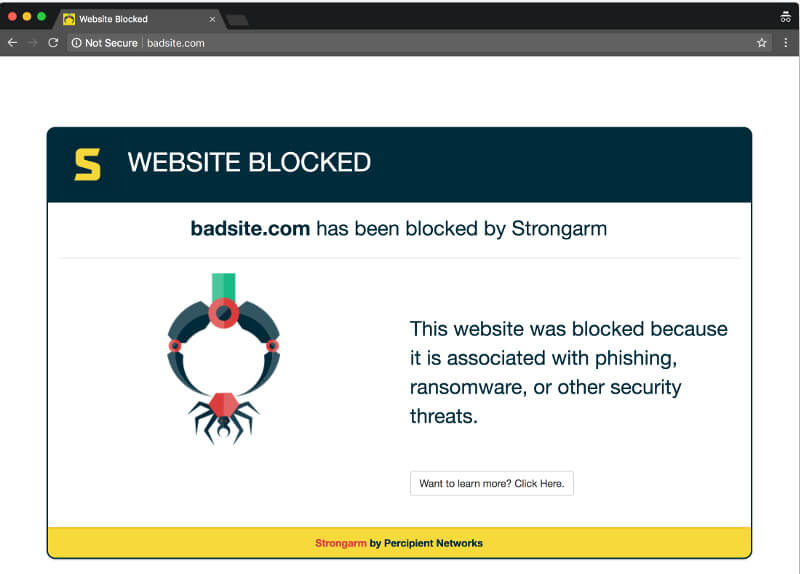
A similar approach is also offered by a range of alternative DNS servers. The premise of these public DNS services is analogous to the Pi-hole: if your computer tries to resolve the domain name of a malicious website (e.g. badsite.com), the server hijacks the DNS request. Public servers typically respond with a false IP address pointing to an informative ‘this website has been blocked’ page.
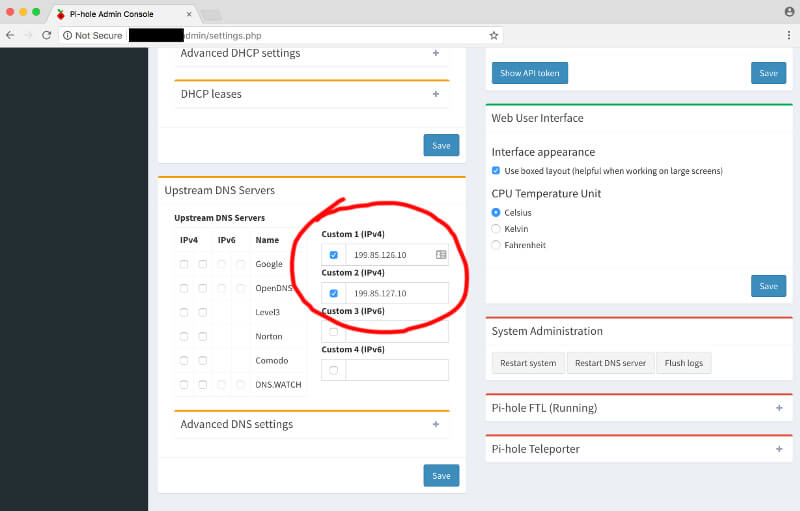
DNS-based blocking is very simple, and it only takes a few steps to configure. You can either change the upstream DNS servers either on your home router or your Pi-hole device. Once DNS queries start going through the third-party servers, you are all set.
List of Threat-blocking DNS Services
We are aware of the following DNS services offering malware blocking and anti-phishing capabilities to home users (as of December 2017):
- OpenDNS Home (comes with admin panel with optional user registration) – 208.67.222.222, 208.67.220.220
- Comodo Secure DNS – 8.26.56.26, 8.20.247.20
- Norton ConnectSafe – 199.85.126.10, 199.85.127.10
- IBM Quad 9 – 9.9.9.9
- Neustar Free Recursive DNS – 156.154.70.2, 156.154.71.2
- SafeDNS (comes with admin panel with optional user registration) – 195.46.39.39, 195.46.39.40
- Comodo Shield (comes with admin panel with optional user registration) – 8.26.56.10, 8.20.247.10
- Strongarm (comes with admin panel with optional user registration) – 54.174.40.213, 52.3.100.184
- Yandex.DNS – 77.88.8.88, 77.88.8.2
- SafeSurfer (paid service, main focus is blocking adult websites) – 104.155.237.225, 104.197.28.121
Disclaimer: Be aware that organisations operating these services will have access to your DNS resolution history, which may allow them to reconstruct your browsing history. If you have privacy concerns over this, have a look at our latest guide on self-hosted malware-blocking DNS servers instead.
But Wait, There’s More!
Certain DNS providers come with an optional admin panel, which typically allows you to:
- View DNS activity on your network (domains allowed/blocked)
- Block website categories (adult, gambling, social media, etc.)
- Block individual domains (e.g. facebook.com)
The following screenshot shows how you can block website categories with Comodo Shield:
Summary
Malware-blocking and anti-phishing DNS servers can be an excellent companion to other anti-malware services, such as anti-malware products and browser plugins. It takes just a few clicks to change the default DNS servers (provided by your ISP) to these third-party servers with the additional protection built-in. Be careful, though! Your DNS requests go a third-party and this may raise some privacy concerns.
Great, so there are almost a dozen providers available. But how we can pick the best DNS service with the most advanced anti-malware capabilities? Their marketing pitch makes them all look the same. Which service is the lemon? In the second part of this article, we help you pick the right DNS service provider.
This article has first appeared in the CryptoAUSTRALIA blog. Image courtesy of Pixabay