Microsoft Exchange is a popular choice for providing email services for businesses. Its email features and seamless integration with Microsoft Outlook are undoubtedly convenient and easy to use, but what about security?
Microsoft Exchange runs exclusively on Windows Server, which in 2017 was affected by various critical vulnerabilities, putting millions of businesses at risk. Exchange also comes with a feature known as Outlook Web Access (OWA) which is designed to allow employees access to their work email remotely. OWA is typically configured with “a relatively lax set of restrictions”, leaving a backdoor to businesses wide-open for cybercriminals.
In the following article, we analyse how Microsoft Exchange Server is abused by cybercriminals to hack into businesses leaving them open to fraud and data theft, and what can you do about them.
Outlook Web Access: The backdoor into your business
The Achilles heel of Microsoft Exchange is Outlook Web Access (OWA). You may only read your emails with the Microsoft Outlook client, but the OWA feature in Exchange allows you to access your mailbox with a web browser. This feature is commonly left running openly on the internet. Unfortunately, this means OWA is an easy way for cybercriminals to get into your business.
By default, OWA only requires a username (or email address) and password pair to allow access to an employee’s mailbox. Alas, industry reports show that one in every two employees are guilty of reusing their passwords across several websites. Sadly, data breaches happen on a regular basis, and passwords are frequently published on the internet for everyone to see.
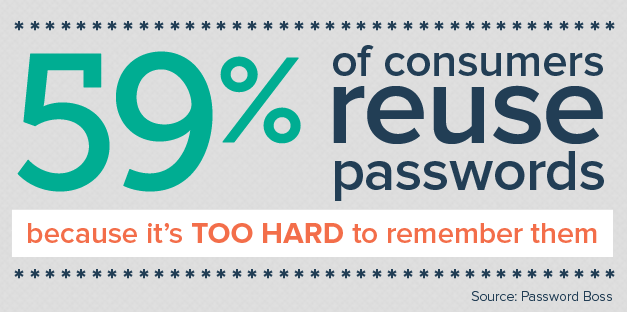
If your business is targeted by a cybercrime group, criminals need to find a valid password which belongs to one of your employees and use it to successfully log into OWA. This is easier as it sounds. All an attacker needs to do is finding an employee in your business, who:
- was involved in a data breach;
- his or her password was leaked to the public;
- routinely reuses their password across several websites.
To make matters worse, highly automated tools are available for cybercriminals to try thousands of username and password combinations per minute on the OWA login page with little to no effort. The more employees you have, the more likely that one of your employees is reusing their favourite (and leaked) password in your business.
Why OWA is an ideal platform for phishing
In addition to the password reuse problem, Outlook Web Access is frequently abused by cybercriminals to steal valid login credentials by cloning your Exchange server’s OWA login page and luring victims into visiting the clone in a phishing campaign.
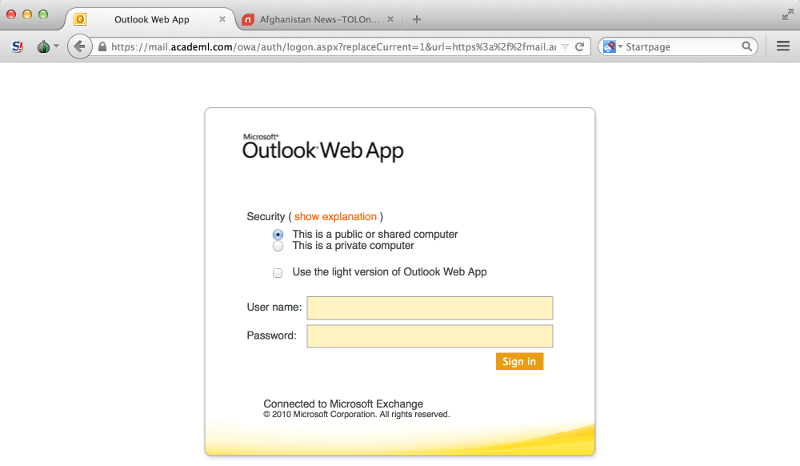
Cybercriminals often target firms with genuine-looking emails (e.g. impersonating system administrators) asking them to click on web links. The password entered on the clone sites then goes straight into the wrong hands. A hacker can then either log into the mailbox with the stolen credentials or sell the password on the dark web for as low as $1.
What happens when the hackers get into OWA?
Once the cybercriminals get a hold on to a valid password, they log into your employee’s email using OWA. They then impersonate the employee in malicious ways such as attempting to misdirect payment instructions, resetting passwords for other online services (DropBox, LEAP, online banking, personal email accounts), or sending further phishing emails to your customers, clients or coworkers.
Unfortunately, it only takes one accidental click by an employee to compromise the security of the computers, tablets and smartphones in your entire office, and become a victim of fraud.
How to protect OWA from unauthorised access
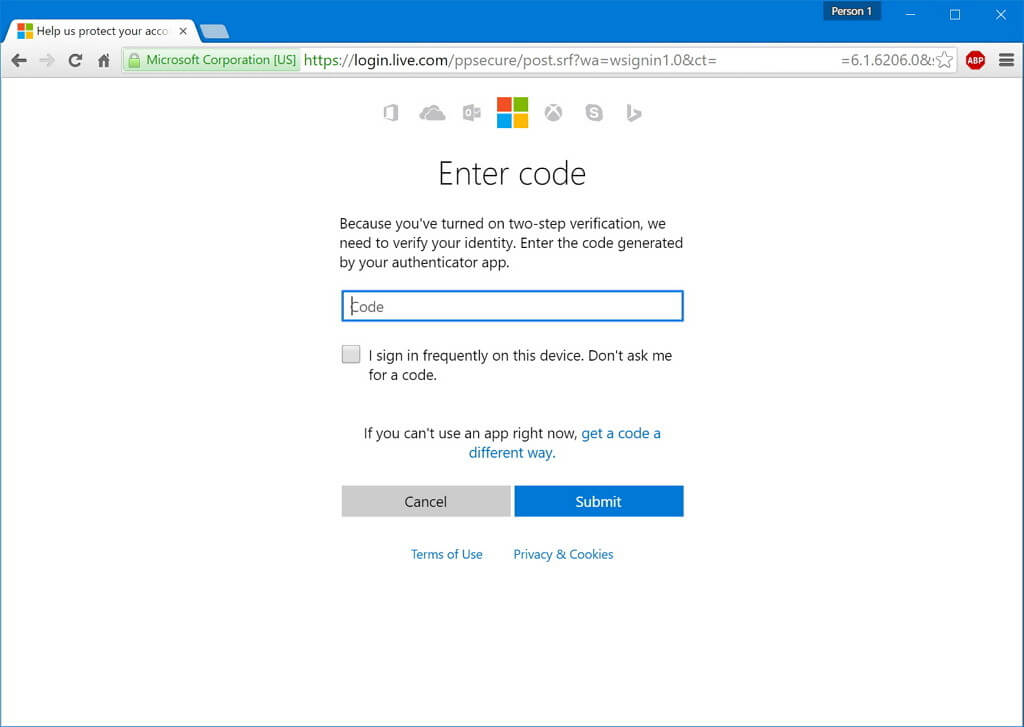
One way to prevent cybercriminals from logging into OWA with stolen or leaked credentials is to implement two-factor authentication (2FA). Although the additional security measure requires your employees to key in a unique, six-digit code beside the password upon login, the extra step prevents criminals from accessing mailboxes even if the valid password is in their possession.
Software vulnerabilities can make you lose your emails for good
Software bugs are an inevitable reality in modern technology. Software vendors, like Microsoft release software patches for fixing critical security bugs. These patches keep products – like Microsoft Exchange – safe and secure from cyber attacks. These security patches should be applied as soon as possible.
Last year, a massive wave of ransomware campaigns (WannaCry, Petya and other variants) demonstrated how forgetful system administrators and negligent IT service providers who fail to patch vulnerabilities in a timely manner (there was a security patch available three months prior to the outbreak) can grind businesses to a halt.
2017 was also the year that WannaCry, Petya and ExplodingCan ransomware variants brought DLA Piper, Qantas and TNT Express to their knees because software patches were not applied on time.
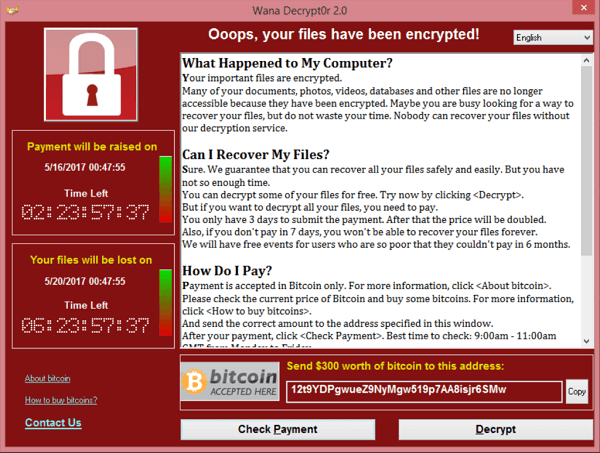
Australian businesses had the first-hand experience in losing control over their important files and emails. They had not only let their customers down but had to spend hundreds of millions of dollars to restore their IT infrastructure.
How to prevent ransomware encrypting your important emails
With self-hosted software, such as Microsoft Exchange, patching becomes the responsibility of your in-house IT staff or IT service provider. Hence, timely patching is essential to prevent a similar disaster from happening to your business.
We recommend you to schedule a discussion with your IT staff or IT service provider today to discuss patching policies and backup practices. Ideally, software updates should be applied with minimal delay and backups should be taken on a regular basis, and tested to make sure they work.
Alternatively, your business should consider migrating to a cloud-based platform such as Office 365 or G Suite. As patching is taken care of by the vendor on a 24/7 basis, meaning your in-hour IT staff or IT service provider does not have to patch your email service.
Lack of phishing protection exposes to cyber attacks
The third reason for not to allow your Microsoft Exchange server to face the internet directly is phishing. By default, Exchange comes with a little to no anti-spam, anti-malware and anti-spam filtering leaving your business exposed to cyber attacks.
Why anti-spam filters will not protect you from phishing
First of all, built-in anti-spam engines are not on the par with anti-phishing technologies. While the Exchange anti-spam engine was built to filter unwanted bulk emails, advanced anti-phishing services are specifically designed to protect organisations from phishing threats.

Anti-phishing services are usually supported by Machine Learning, AI and Threat Intelligence technologies all looking for specific red flags of phishing attempts. The telltale signs include typical wording and text semantics, invalid digital signatures, unusual sending patterns and poor sender reputation. File attachments are also analysed in safe sandbox environments for known and unknown threats, and embedded hyperlinks are modified to perform a real-time analysis of any website when the recipient clicks on them. These sophisticated technologies are only available in anti-phishing services.
Anti-malware is not anti-phishing
The anti-malware feature built into Microsoft Exchange is based on the Microsoft Defender anti-malware engine. According to independent anti-malware product tests, Microsoft Defender routinely performs poorly compared to its competitors when it comes to blocking malware. A recent report by MRG Effitas found that Microsoft Defender fails to recognise a virus once in every fifty cases.
If your business regularly receives emails with file attachments from your clients or customers, the chances are that Windows Defender is going to miss a malicious file attachment.
How you can protect your Exchange service from phishing
The built-in anti-malware engine can be replaced with third-party anti-malware products. However, they typically involve additional licensing costs and require specialised IT expertise. Furthermore, anti-malware products lack specific anti-phishing technologies that anti-phishing services provide.
As for the anti-spam engine in Exchange, we suggest replacing the built-in filter with a third-party anti-phishing service. Numerous cloud-based and on-premise solutions are available. In our previous article, we reported what the top choices of anti-phishing products of top-tier and mid-tier law firms are in Australia.
Summary
Poor patching practices, password reuse, malware and phishing can put Australian businesses running Microsoft Exchange at risk. Firstly, important files and emails could be lost forever due to ransomware attacks. Secondly, Outlook Web Access (OWA) is an ideal playground for cybercriminals to discover valid passwords belonging to your employees. Last, but not least, phishing exposes businesses to all sorts of scams, usually with financial motivations.
Although each cyber challenge from above can be addressed separately by applying a rigorous software patching policy and two-factor authentication, we suggest migrating to cloud-based service instead. On platforms like Office 365 and G Suite, patching is managed by the vendor, and two-factor authentication is available as a built-in security feature.
As for mitigating the phishing threat, we recommend adding an additional layer of cloud-based anti-phishing technology to protect your business from threats before they reach your mail server.
About Iron Bastion
Iron Bastion are Australia’s anti-phishing experts. We offer all businesses the same anti-phishing technology used by big businesses, without the big-business pricing.
Our range of services are cloud-based, fully managed and easily integrate with your existing infrastructure. Our team feature qualified cybersecurity experts, and all our staff and operations are based in Australia.
Contact us for a free consultation, or sign up for a 14-day free trial of our services today.
* * *
This article has first appeared on the Iron Bastion blog and was co-written with Nicholas Kavadias.
