Slides on Subresource Integrity from the SecTalks Sydney meetup
Tag: sri

Upcoming Features of Subresource Integrity 2.x
As a response to the growing number breaches involving CDNs, the first release of the Subresource Integrity (SRI) was published hastily in late 2015. The W3C WebAppSec Working Group decided to leave certain useful features out, in favour of an early release. Although SRI already does the job, there is some room for improvement with regards to user experience. The good news is that some of these features will be added to the next iteration of SRI.
The following article gives a brief, speculative overview of the upcoming features of Subresource Integrity.
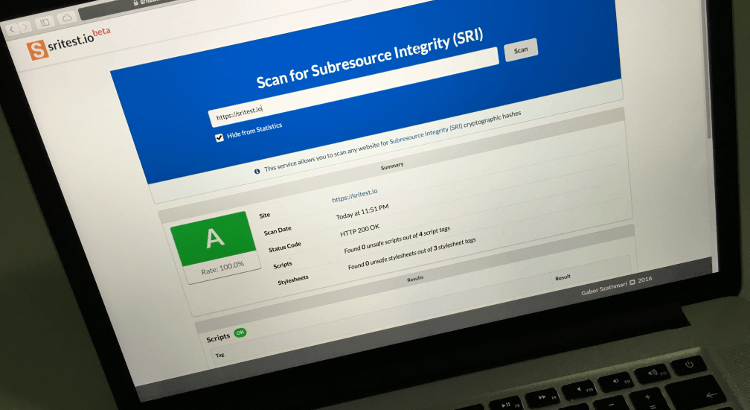
sritest.io February Update
Semi-regular updates on the improvements, bugfixes and other changes to the Subresource Integrity scanner at sritest.io
Compromising US Banks with Third-party Code
Online banking services of major banks in the US can potentially be compromised through third-party services. Banks are including JavaScript code from external sources controlled by someone else. This practice opens up the possibility of stealing online banking passwords, diverting payments or draining bank accounts.
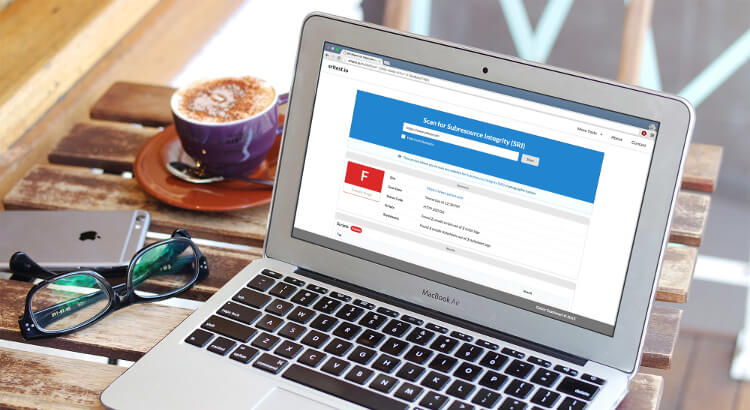
Scanning Websites for SRI Hash Usage with sritest.io
Third-party hosted website assets, such as JavaScript libraries, are vulnerable to tampering. However, a new technique named Subresource Integrity (SRI) is here to protect these external assets.
One problem is the slow implementation of SRI, thus sritest.io was born. The new service enables website owners and frontend developers to evaluate their sites for SRI hash usage. Sritest.io aims to help the widespread implementation of SRI, thus, ultimately protect website visitors from malicious code.
