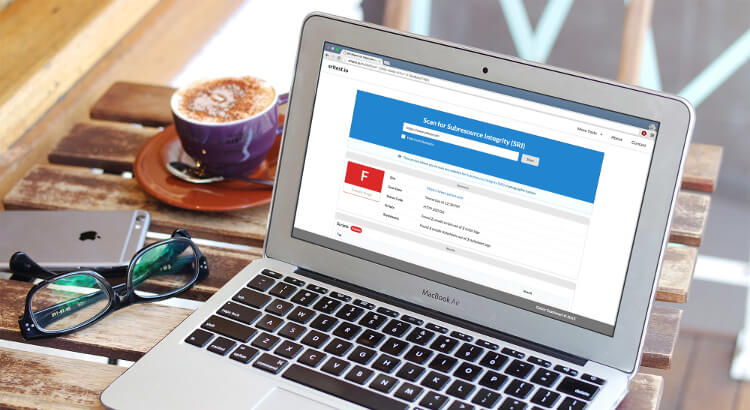
As a response to the growing number breaches involving CDNs, the first release of the Subresource Integrity (SRI) was published hastily in late 2015. The W3C WebAppSec Working Group decided to leave certain useful features out, in favour of an early release. Although SRI already does the job, there is some room for improvement with regards to user experience. The good news is that some of these features will be added to the next iteration of SRI.
The following article gives a brief, speculative overview of the upcoming features of Subresource Integrity.