Passwords suck, bit time. They should be unique per each website, and we are supposed to remember all of them. Password cards help to remember the myriad of passwords. Sadly, these cards are vulnerable to brute-forcing attacks and here is why.
This post introduces a tool called Munchkin, which is a wordlist generator for attacking passwords derived from password cards.
What is a Password Card?
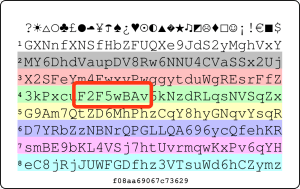
Password (aka. grid) cards contain a block of random characters in a matrix-like pattern. To generate a password for a website, any series of characters can be chosen from the card. The main idea is that it’s easier to remember the initial location, the reading direction and password length from the card – than memorising the password itself.
In the example above, Alice chose “F2F5wBAv” from the card as her password. She only needs to remember that the password:
- Starts at row 4 and the column with a black dot
- Have eight (8) characters
- Direction is left to the right
Security of the Card

The card is generally printed on a piece of paper and kept in a safe location such as a wallet. In other words, password security heavily relies on physical security.
Even if the card gets into an attacker’s possession, the secrets cannot be quickly recovered. The standard card from passwordcard.org contains 238 characters spanning 8 rows and 29 columns.
To guess a password, the attacker must know several parameters such as the initial location, reading direction, and the password length. That’s a lot of combinations! So it must be a difficult process to get all the passwords, isn’t it?
It’s true until we start automating things.
Munchkin, the Wordlist Generator
Password guessing attacks rely on wordlists, which may originate from simple dictionary words (aspell). Sophisticated wordlists are based on topic-specific wordlists (Star Trek, Monty Python), generic password variations (crunch wordlist generator) or compromised passwords like clear-text passwords from the RockYou breach.
Munchkin is a wordlist generator tool that generates relevant lists of potential passwords based on password cards.
Software Highlights
- Supports 8 different card reading strategies (e.g. left-to-right, diagonal, zig-zag)
- Built-in support for passwordcard.org cards
- Custom cards are also supported
- Able to generate passwords of any length
Usage Example
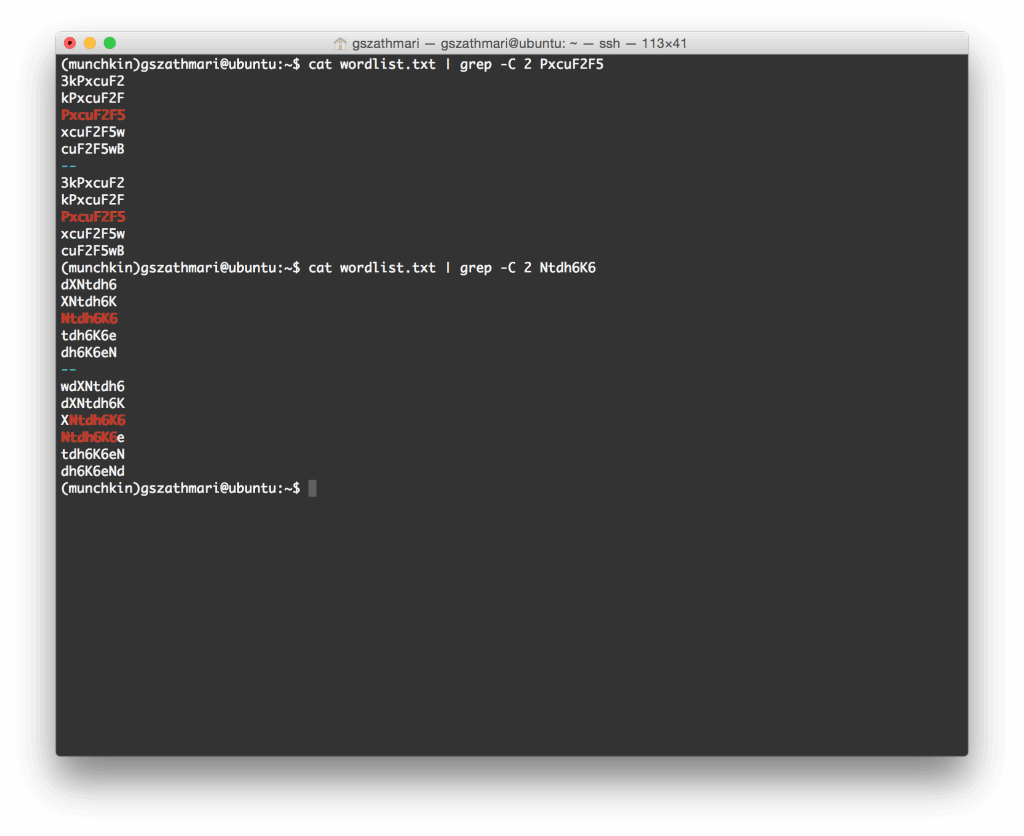
A user named Bob generates a card from passwordcard.org with an initial seed of f08aa69067c73629. He chose two passwords for his Gmail and Facebook accounts, “PxcuF2F5″ and “Ntdh6K6″ respectively.
When Bob takes out his password card to log into Gmail, he gets sloppy and leaves it on his desk while he steps out for a nice Vegemite sandwich. Mallory seizes the opportunity and takes a sneaky photo of the unattended card.
Mallory then downloads Munchkin from PyPI. He punches in the initial seed from Bob’s card, then generates a comprehensive wordlist as the following:
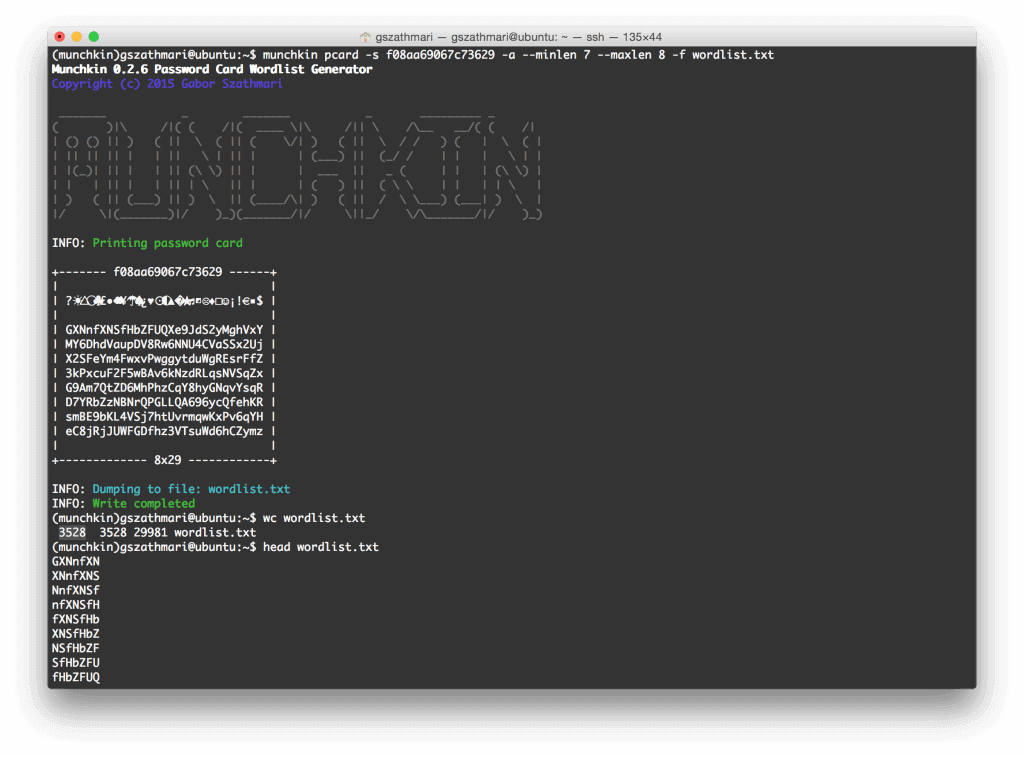 Mallory collects 3528 possible passwords into the wordlist.txt file. It is small enough to brute-force Bob’s Gmail account with Hydra through the SMTP service in a relatively short amount of time. (Update 4/5/16: Fixing broken link. Also, more recent guides mention that Google locks the user account after a hundred-odd attempts. Probably some other example would’ve been more appropriate.)
Mallory collects 3528 possible passwords into the wordlist.txt file. It is small enough to brute-force Bob’s Gmail account with Hydra through the SMTP service in a relatively short amount of time. (Update 4/5/16: Fixing broken link. Also, more recent guides mention that Google locks the user account after a hundred-odd attempts. Probably some other example would’ve been more appropriate.)
As one can see, both of Bob’s passwords are in the generated word list:
Python Package and Source Code
Grab the package built for Python 2.x and the source code from the following links:
As always, pull requests are welcome!
Image Courtesy of Reuters