Internet censorship makes the Internet insecure. While the big ISPs in the UK and other countries are blocking file sharing websites such as The Pirate Bay or KickassTorrents, movie-lovers have different alternatives to circumvent these restrictions. One popular method to overcome the filtering is using mirrors.
Torrent mirrors are essentially reverse proxies, which are forwarding HTTP traffic between the UK and the original sites hosted elsewhere. Data supposed be left intact and the only difference should be the address in the URL bar.
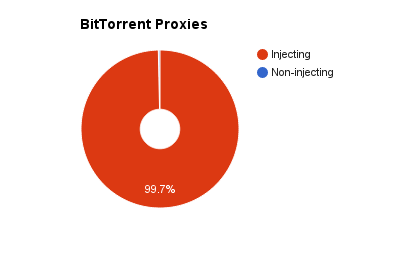
This experiment proves however that 99.7% of the tested torrent mirrors are injecting additional JavaScript into the web browsing traffic. A great share of these scripts serve content with malicious intent such as malware and click-fraud.
Dissecting the Torrent Mirrors
Several websites (1, 2, 3) exist for hosting up-to-date proxy URLs for those with censored Internet connections. The links are usually grouped by file sharing services, and rated by speed and reliability.
Anyone may submit a link to a new mirror, which is usually added to these websites after some sort of manual approval.
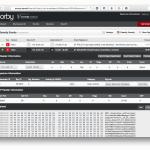
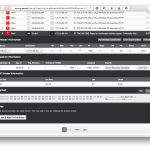
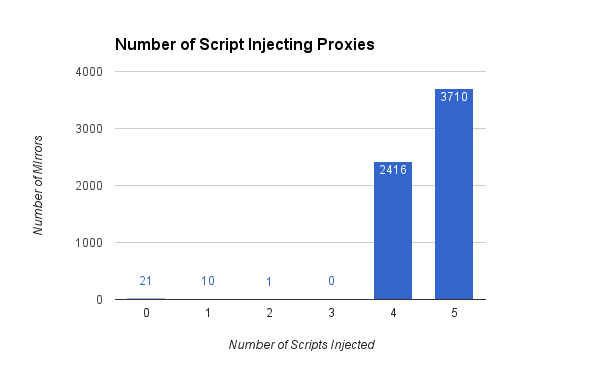
Over 6,000 online mirrors from these link farms have been inspected in the experiment. The test was relatively simple: the HTML source of the original torrent site such as The Pirate Bay was compared to its mirrors. Any difference between between inline scripts (<script></script> tags) or external scripts (<script src=””>) meant the mirror is injecting additional JavaScript code into the traffic.
Test Results
The experiment shows that the vast majority of the mirrors are injecting additional content into the traffic.
Need for Tooling
In order to produce these results above, I developed a new application to identify the injected scripts. Although my test was inspired by a similar experiment involving free forwarding proxies, I had to develop my own tool because torrent mirrors are reverse proxies.
gszathmari/proxy-buster
Compare two websites for unwanted extra JavaScript
Source code and further documentation of is available on GitHub. Pull requests are welcome!
Dissecting a Malicious Mirror
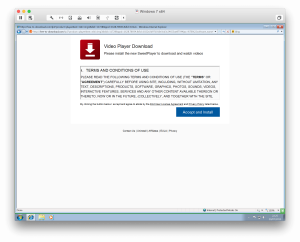
So what the injected scripts mean to the end-users? Let’s choose a mirror with a lot of unwanted scripts and find it out! I set up a virtual environment with an unpatched Windows 7, outdated Flash and browser. Although advanced exploit kits are capable to detect VMs, my focus was to inspect the misleading ads and unwanted downloads.
Choosing a High-Risk Site
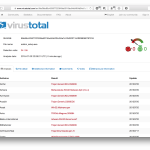
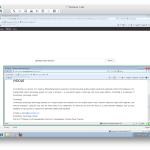
I pseudo-randomly chose hxxp://extratorrent.kat.tf, an Extratorrent mirror with 5 additional scripts compared to the original thing on http://extratorrent.cc. This mirror included the following extra pieces of JavaScript:
Scripts between line 2-4 seems to be legitimate and harmless, but what about proxyads.net? Let’s have a look!
Wow, this is a big pile of mess! We need to descramble and beautify the code to get the idea what is going on. Here is the result with the standard GA tracker removed:
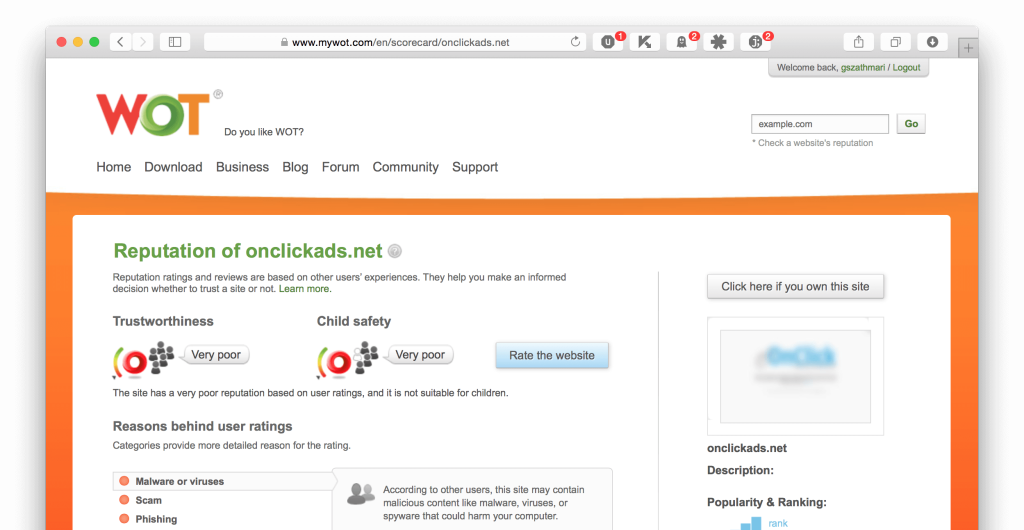
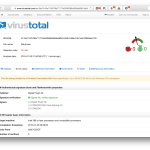
This snippet loads external scripts from onclickads.net (line 1.) and happens to have a poor reputation on Web of Trust.
OSINT
All of the three injected domains (line 1-3.) were registered by PropellerAds Media. The connection between them is the same registered PO Box address on the Virgin Islands found in the WHOIS records and Ghostery. While banners are usually served from mobisla.com and mobtrks.com, the popunders are launched from onclickads.net.
This company promises “Payouts 200% higher than anywhere else due to detailed optimization […] and selecting the best performing campaigns”. Although PropellerAds was associated with malvertising in 2013, their website claims that all advertisers are vetted.
An interesting thing is that the popunder script from onclickads.net is heavily obfuscated. Although the analysis is out of scope this time, I made the paste available here for the adventurous.
As for the mirror owner, the domain kat.tf has been registered by Liam Khan according to the WHOIS. Mr. Khan apparently owns several domains hosting other torrent mirrors.
Malware Distribution
Let’s see what happens when I pop hxxp://extratorrent.kat.tf into my browser. First of all I got several popups of fake Flash updates and video codecs straight away.
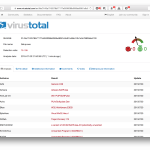
I downloaded the files of course, and uploaded them to VirusTotal. About half of the AVs flagged the files as malware. An interesting thing was that one file had a valid code signing signature.
I also had Suricata (Snort replacement) with the free EmergingThreats rules running in my lab, which was alerting on the suspicious traffic.
Installing the Malware
I have installed one of the files included, which turned out to be a browser hijacker software. It changed my default search provider to www.oursurfing.com. Needless to say, this search engine also has a bad reputation on WoT.
Click Fraud
My computer was also participating in click-fraud. One of the scripts loaded from the Torrent mirror was generating fake views of some car racing videos in the background.
The http.log of Suricata indicates that the click-fraud was carried out by one of the additional scripts and not the malware. It is because this type traffic had stopped once I closed my web browser.
Conclusion
Numerous ISPs are blocking access to popular torrent sites for copyright purposes. Internet censorship has created thousands of mirrors that provides access to the censored file sharing sites. Although some of them are operated by good citizens, the majority is monetising the situation by injecting unwanted ads, distributing malware and involving their visitors in click-fraud.
The list of examined websites with some additional stats is available here.
Update (05/08/2015): Here is a breakdown of the domains and a diagram showing the external script domains. The PropellerAds ad was loaded from proxyads.net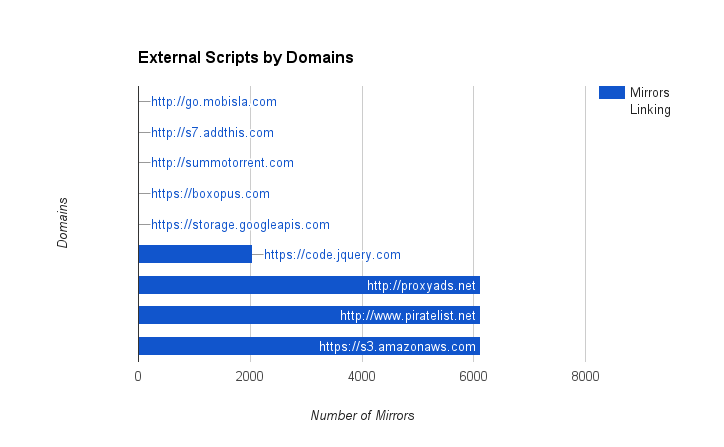
The full output (all external and inline scripts) of proxy-buster is also available here.
Update (06/08/2015): Coverage on TorrentFreak
Update (07/08/2015): proxyads.net (operators of piratelist.net) has contacted TorrentFreak with a promise of resolving the issues with PropellerAds. I will update when I learn more about the outcome.
Update (20/08/2015): Additional coverage on International Business Times, Business Reporter, TechWorm, GadgetHub, LaatsteNieuws.io, VPN Compare, Ecumenical News
Update (14/10/2015): Mirrors of Piratelist.net mysteriously disappear, TorrentFreak reports
Photo courtesy of kris krüg