Two out of three small business owners believe a cyberattack to their business is unlikely, but in reality, the same proportion of businesses has been victims of cyber attacks, according to Keeper Security. The direct consequences of a cyberattack is disruption of your business, loss of productivity and revenue, which may lead to the loss of business reputation, the loss of existing and future clients and unwanted media attention.
Therefore, it is critical to keep your small business secure from cyber attacks, but how? With the following three simple measures, you can quickly improve the risk profile of your business.
Enable two-factor authentication
There is a lot of confusing and often contradicting advice about password security. While some believe a password should be complex (P@ssw0rd1), others reckon it must be long and memorable (CorrectHorseBatteryStaple) instead. The collective wisdom is to change passwords regularly, and experts suggest a password should be unique. So, who is right?
No matter what advice you follow, the best thing for your business in terms of cybersecurity is two-factor (aka. multi-factor, two-step or 2FA) authentication enabled.
You might be familiar with the concept of two-factor authentication already. Online banking typically requires you to enter a six-digit code from your mobile phone to confirm a new payee or a bank transfer. This practice is a strong security measure banks rely on to keep the accounts secure. According to proponents, two-factor authentication reduces the incidence of identity theft and online fraud.
 Conversely, 2FA can protect your favourite services as well. Business email providers (Office 365, G Suite), cloud drives (Dropbox, OneDrive, Box), accounting software (Quickbooks, Xero) and many others already support two-factor authentication out of the box.
Conversely, 2FA can protect your favourite services as well. Business email providers (Office 365, G Suite), cloud drives (Dropbox, OneDrive, Box), accounting software (Quickbooks, Xero) and many others already support two-factor authentication out of the box.
For a comprehensive list of platforms supporting 2FA, visit twofactorauth.org. To enable two-factor authentication on a specific service, check the illustrated guides and step by step instructions on the Turn It On website.
Deploy the right antivirus software suite
Not all antivirus software is equally effective. Contrary to popular belief, free and low-cost antivirus software may lack the advanced features that keep your business safe from the sophisticated cyberattacks of today.
What your business needs to keep the nasties away is an endpoint security solution. As opposed to traditional antivirus products, they cover your entire network and protect against a wide range of cyberattacks.
For example, better endpoint security solutions come with ransomware protection, phishing protection, safe banking and browser protection features. Moreover, high-end products tend to bundle VPN services, password managers, or data backup solutions along with the core product.
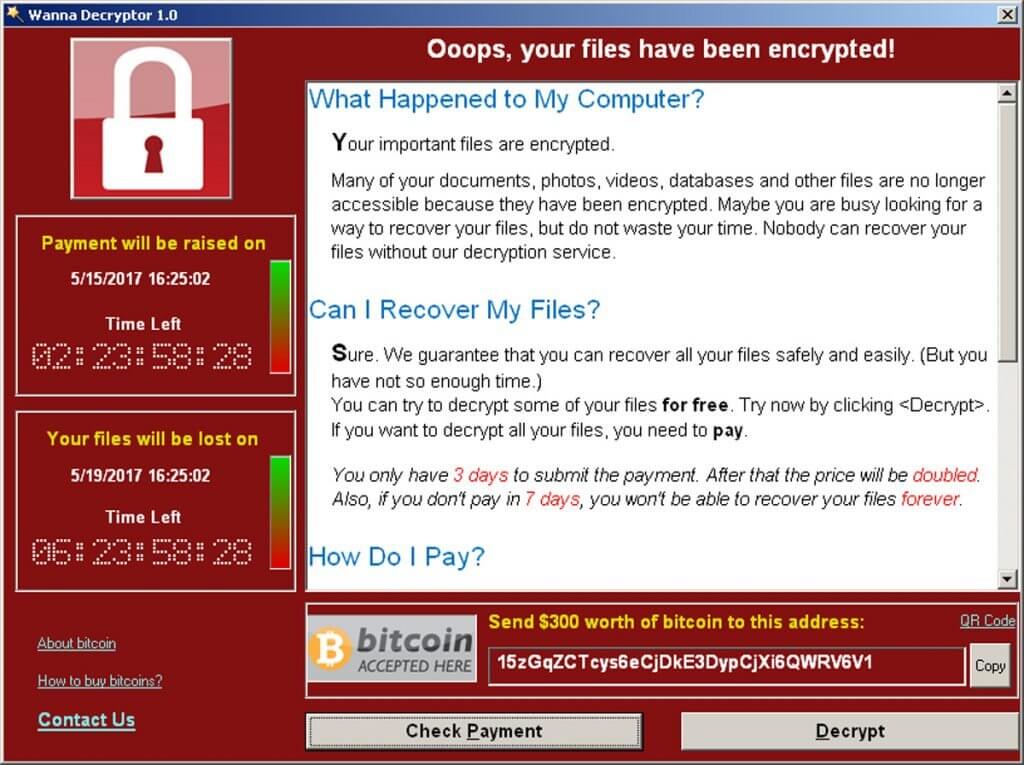
As for the antivirus feature of free and low-cost solutions, they often fail to protect from the more advanced attacks. Independent antivirus assessments demonstrate that specific antivirus solutions struggle with blocking sophisticated threats like financial malware and software exploits.
If you are in doubt whether your business is being protected by the right product, refer to these independent antivirus reports to choose the right brand and software edition. Alternatively, talk to a professional such as your service IT provider for expert advice.

Back up your data regularly
Does your business rely on important files and emails? Will you be able to provide your services if the business files and clients’ emails suddenly disappear? Will your company manage to stay afloat with your business-critical data being wiped off?
If your answer to any of these questions is ‘no’, you need to have a backup plan.
Data backup as a practice stretches back in time as far as the 1950s. The first generation of computers was built from vacuum tubes and rotating magnetic drums, and they relied on punch cards to manage data and programs. Back in the day, additional copies of punched cards were printed to restore data in case they got corrupted or missing.

The concept of data backup has not changed since the early 50s. Computer crashes, data corruption, and other disasters are still inevitable in the days of modern computing. On top of that, we have new threats such as ransomware attacks. Hence your irreplaceable files and emails should be backed up regularly to keep your business running.
A time-tested backup practice follows the ‘3-2-1 Backup Rule’:
- keep three (3) copies of your data,
- store two (2) backup copies on different storage media,
- with one (1) of them located offsite.
The backup storage media may include, but not limited to:
- external hard drives
- flash drives
- optical disks
- magnetic tapes; and
- cloud-based file storage solutions.
As for the offsite rule, cloud drives and portable devices satisfy the requirement. The important thing is to keep a separate copy far from the office to protect your data from adverse events such as fire, flood or theft.

To start backing up your data today, consider subscribing to an automated backup solution such as Crashplan or Backblaze. For a more robust backup strategy that satisfies the 3-2-1 rule, please consult your IT provider. Advanced solutions are available to provide comprehensive protection for your servers, databases, mailboxes and portable devices.
Summary
If there is one thing you can do today to make your business more secure, enable two-factor authentication on your business email service. Your mailbox not only contains sensitive information, but your email address is the gateway to other services through the ‘Forgotten Password’ feature. The majority of data breaches is due to email hacking.
In case you have not purchased an endpoint security solution for your business, do yourself a favour and buy one. You will be protected from sophisticated threats, ransomware and run-of-the-mill phishing attacks right away. The endpoint solution pays for itself after the first attack it manages to block.
If you are not carrying out backups regularly, we recommend you subscribe to an automated backup solution right away. A data disaster can happen any time, your important files need to be backed up immediately. For a long-term backup plan, we suggest consulting a professional fora more comprehensive and cost-effective solution.
The author is an IT and cybersecurity expert with over ten years of experience, having worked in both the private and public sectors in Australia and overseas. He has worked with numerous clients such as Amazon, Ausgrid, The Walkley Foundation and NSW eHealth. His projects include data breach investigations, security incident management, phishing protection and cyber risk management.
Gabor is now helping small businesses with their IT challenges at Arrow Networks, a managed services provider offering IT and cybersecurity solutions for small businesses.
Get in touch with their friendly team today to discuss how they can help you.
This article has first appeared at Clarity Tax Consulting on 2 September 2019.
